The threat actors behind the BlackRock and ERMAC Android banking Trojans have unleashed yet another piece of malware for rent. needle Introduces new capabilities to access files stored on the device and create remote interactive sessions.
ThreatFabric, report Sharing with The Hacker News, Hook was characterized as being a novelty ERMAC fork advertised as having “all the features of its predecessor” but selling for $7,000 a month.
“Additionally, we add Remote Access Tool (RAT) capabilities to our arsenal, joining the family that can perform full device takeover (DTO) such as Octo and Hydra to complete the complete deception chain. All intermediate steps can be used to extract PII into transactions without the need for additional channels,” said the Dutch cybersecurity firm.
The majority of financial apps targeted by malware are located in the United States, Spain, Australia, Poland, Canada, Turkey, United Kingdom, France, Italy, and Portugal.
At the hands of a threat actor known as DukeEugene, Hook is the latest evolution of ERMAC, which was first published in September 2021, and is the latest evolution of another Trojan named Cerberus whose source code was leaked in 2020. Based on a wooden horse.
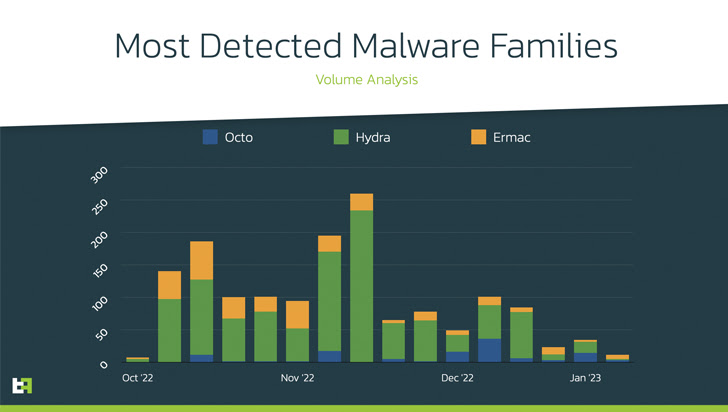
“Ermac has consistently lagged behind Hydra and Octo in terms of features and functionality,” ThreatFabric researcher Dario Durando told The Hacker News in an email. “This is also known among attackers who prefer these two families over Ermac.”
“The lack of some sort of RAT functionality is a big problem for Android Bankers these days, as it doesn’t offer the possibility to perform a device takeover (DTO). DTO is the most likely to succeed and It is a fraudulent technique that goes undetected by fraud scoring engines or fraud analysts.
Like other Android malware of its kind, the malware exploits Android’s Accessibility Service APIs to perform overlay attacks, including contacts, call history, keystrokes, two-factor authentication (2FA) tokens, and even WhatsApp messages. , to collect all kinds of confidential information.
It also flaunts an extended list of apps, including ABN AMRO and Barclays, and the malicious sample itself masquerades as the Google Chrome web browser to trick unsuspecting users into downloading the malware.
- com.lojibiwawajinu.guna
- com.damariwonomiwi.docebi
- com.yecomevusaso.pisifo
Other key features added to the hook include the ability to remotely view and interact with the infected device’s screen, retrieve files, extract seed phrases from crypto wallets, and track phone location. It has features and blurs the line between spyware and banking malware. .
ThreatFabric said the hooking artifacts it has seen so far are in the testing stage, but noted that they could be delivered in the form of phishing campaigns, Telegram channels, or dropper apps on the Google Play store.
“The main drawback of creating new malware is usually enough trust from other actors, but given DukeEugene’s status among criminals, this may not be a problem for hooks. is very high,” says Durando.


