A zero-day vulnerability in the Windows installer of Atera remote monitoring and management software could act as a springboard to launch a privilege escalation attack.
The flaws discovered by Mandiant on February 28, 2023 were assigned the following identifiers: CVE-2023-26077 and CVE-2023-26078the issue was fixed in versions 1.8.3.7 and 1.8.4.9 released by Atera on April 17, 2023 and June 26, 2023 respectively.
“The ability to initiate operations from the NT AUTHORITY\SYSTEM context can pose a potential security risk if not properly managed,” said security researcher Andrew Oliveau. Said. “For example, if the settings are incorrect, custom action Running as NT AUTHORITY\SYSTEM could be exploited by an attacker to perform a local privilege escalation attack. “
Successful exploitation of such a vulnerability could open the way to arbitrary code execution with elevated privileges.
Both flaws exist in the repair functionality of the MSI installer and can lead to scenarios where the operation is triggered from the NT AUTHORITY\SYSTEM context even if the operation was initiated by a standard user.
According to a Google-owned threat intelligence firm, Atera Agent is susceptible to local privilege escalation attacks, which can be exploited. DLL hijack (CVE-2023-26077) It is possible to exploit this to get a command prompt as the NT AUTHORITY\SYSTEM user.
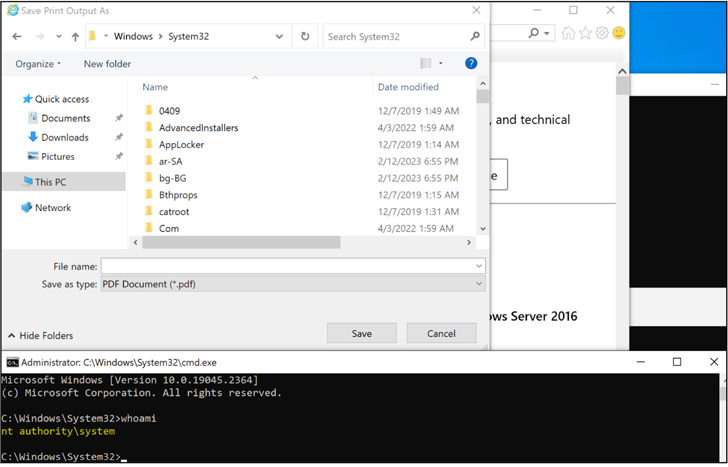
CVE-2023-26078, on the other hand, involves “executing a system command that triggers the Windows Console Host (conhost.exe) as a child process,” which opens a “command window” that, “when run with elevated privileges, may allow an attacker to exploit this command window to perform local privilege escalation attacks.”
“Misconfigured custom actions can be easily identified and exploited, and as a result can pose significant security risks to your organization,” said Oliveau. “It is imperative that software developers thoroughly review their custom actions to prevent attackers from hijacking NT AUTHORITY\SYSTEM operations caused by MSI remediation.”
Shielding Against Insider Threats: Mastering SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join us for this webinar to explore practical strategies and proactive security secrets using SaaS Security Posture Management.
This disclosure was made as Kaspersky hut A critical privilege escalation flaw in Windows (CVE-2023-23397, CVSS score: 9.8) has been fixed to further expose the issue being exploited in the wild by threat actors using specially crafted Outlook tasks, messages or calendar events.
Microsoft previously disclosed that a Russian nation-state group had been weaponizing this bug since April 2022, but here’s evidence gathered by antivirus vendors: clearly The actual exploitation attempt was carried out by an unknown actor targeting governments and critical infrastructure organizations in Jordan, Poland, Romania, Turkey, and Ukraine a month prior to public disclosure.


