The attack surface is growing faster than security teams can keep up. To stay ahead, you need to know what is being exposed and where attackers are most likely to strike. With the move to the cloud dramatically increasing the number of internal and external targets, prioritizing threats and managing the attack surface from an attacker’s perspective is more important than ever. Let’s see why it’s increasing and how to properly monitor and manage it with tools like: invader.
What is your attack surface?
First, it is important to understand that attack surface is the sum of digital assets that are “exposed”, whether they are secure or vulnerable, known or unknown, or in active use. is. This attack surface continually evolves over time and includes digital assets located on-premises, in the cloud, subsidiary networks and third-party environments. So anything a hacker can attack.
What is attack surface management?
Attack surface management is the process of discovering these assets and services and reducing or minimizing their exposure to prevent exploitation by hackers. Exposure has two meanings. One is current vulnerabilities such as missing patches and misconfigurations that make services and assets less secure. But that can mean exposure to future vulnerabilities.
Consider a management interface such as cPanel or a firewall management page. These may be safe against all known attacks today, but tomorrow a vulnerability is discovered in the software that could instantly become a significant risk. Assets don’t have to be vulnerable today to be vulnerable tomorrow. Reducing your attack surface makes tomorrow’s attacks harder, regardless of vulnerability.
Therefore, an important part of attack surface management is to reduce exposure to future vulnerabilities by removing unnecessary services and assets from the Internet. This was the impetus for Infringement of Deloitte Describes the difference from traditional vulnerability management. But to do this, you first need to know what’s out there.
Asset management and vulnerability management
Although often considered unrelated to vulnerability management, asset management has traditionally been a labor-intensive and time-consuming task for IT teams. Even with control over hardware assets within the organization and within the network perimeter, problems still abounded. Exfiltration of just one asset from the asset inventory could bypass the entire vulnerability management process and, depending on the sensitivity of the asset, could have far-reaching business impact.
Today it’s much more complicated. Companies are moving to his SaaS, migrating systems and services to the cloud, internal teams are downloading their own workflow, project management and collaboration tools, and individual users expect to customize their environment. I’m here. As companies expand through mergers and acquisitions, they often inherit systems they are unaware of.A typical example is that telecommunications company TalkTalk Compromised in 2015 Up to 4 million unencrypted records were stolen from systems they didn’t even know existed.
Move security from IT to DevOps
Today’s cloud platforms allow development teams to move quickly and scale as needed. However, this shifts much of the responsibility for security into the hands of development teams, moving away from traditional centralized IT teams with robust and reliable change management processes.
This means cybersecurity teams struggle to see what’s going on or discover where assets are. Similarly, when large companies and teams are distributed around the world, it becomes increasingly difficult to know where all the systems are located.
As a result, organizations increasingly understand that their vulnerability management process must be incorporated into a more comprehensive “attack surface management” process. This is because before you can think about what your vulnerabilities are and what you need to fix, you first need to know what you are exposing to the Internet. Prioritize.
Key Features of Attack Surface Management Tools
Various tools on the market can help you find assets, find new domains like yours, and find websites with content similar to yours. Your team can then see if this is a company asset and choose whether to include it in your vulnerability management process and how to protect it. However, this requires internal resources as the tool cannot do this.
Similarly, some tools focus only on the external attack surface. However, a common attack vector is through employee workstations, so attack surface management should also include internal systems. Here are his 3 essential features that every person needs. attack surface monitoring tools You must provide:
1. Asset Discovery
You can’t manage an asset if you don’t know it exists. As we have seen, most organizations have various There is an “unknown”. Intruder’s CloudBot checks every hour for new IP addresses or hostnames for connected AWS, Google Cloud, or Azure accounts.
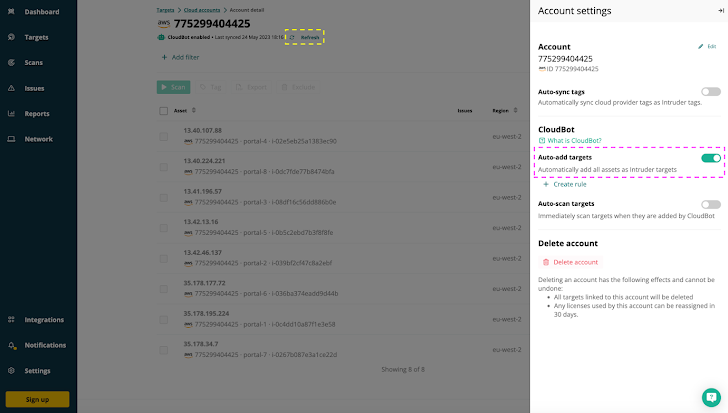 |
| Intruder’s CloudBot automatically adds new external IP addresses or hostnames in your cloud account for monitoring and vulnerability scanning. |
2. Business background
Not all attack vectors are created equal, and “context” (what is exposed to the internet) is an important part of attack surface management. Traditional tools do not provide this context. Prioritizing vulnerabilities is difficult because all attack surfaces (external, internal offices, internal data centers) are treated the same. Attack surface management tools identify internal and external security control gaps and expose security weaknesses that need to be addressed and remediated first.
Intruder takes this one step further, providing insight into the business units to which specific assets and applications belong. For example, knowing if the compromised workload was part of a critical application managing her SWIFT transactions between banks would help her develop a remediation plan.
3. Proactive and reactive scanning
You can’t test your attack surface just once. It continues to grow daily as new devices, workloads and services are added. As it grows, so does the security risk. Along with the risk of new vulnerabilities, there is also the risk of misconfigurations, data breaches, and other security gaps. It’s important to test all possible attack vectors, and it’s important to continually test to keep your understanding from becoming stale.
Even better than continuous scanning is a platform that can scan proactively or reactively depending on the situation. For example, start scanning to keep up with new cloud services coming online, or proactively scan all your assets as soon as new vulnerability checks are available.
Reduce your attack surface with Intruder
Tools to monitor your attack surface invader Do all this and more. Intruder makes sure everything connected to the internet is the way it should be by making it easy to find and explore. Its network view feature shows exactly which ports and services are available, including screenshots of which ports and services websites and apps are running on.
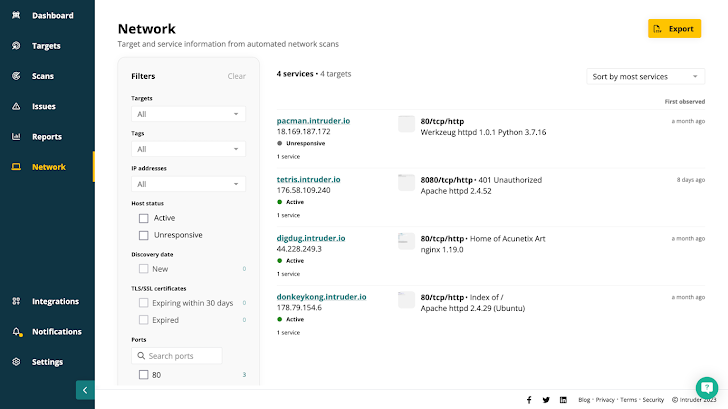
Most automation tools are great at spewing data out for analysts to see, but not at reducing the “noise.” Intruder prioritizes issues and vulnerabilities based on context or whether they should be on the internet in the first place. Combined with Intruder’s continuous monitoring and scanning for new threats, it makes it easier and faster to find and fix new vulnerabilities before they can be exploited.
Try Intruder for yourself!
Intruder solves one of the most fundamental problems in cybersecurity with its attack surface monitoring capabilities. It means understanding how attackers see your organization, where they might get in, and how to identify, prioritize, and eliminate risks.ready to start ?


