The recent attack on Microsoft’s email infrastructure by Chinese nation-state actors dubbed Storm-0558 is said to be more widespread than previously thought.
According to cloud security firm Wiz, the inactive Microsoft Account (MSA) consumer signing key used to forge Azure Active Directory (Azure AD or AAD) tokens to gain unauthorized access to Outlook Web Access (OWA) and Outlook.com could have also enabled attackers to forge access tokens for various types of Azure AD applications.
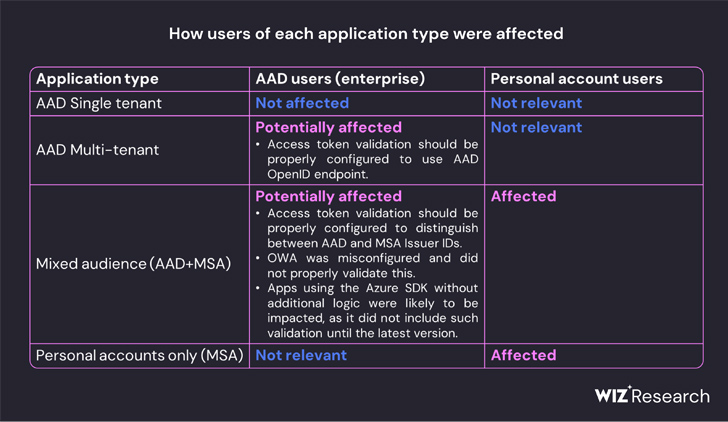
this It contains Any application that supports personal account authentication, such as OneDrive, SharePoint, and Teams. Customer applications that support the “Login with Microsoft feature” and multi-tenant applications under certain conditions.
“Everything in the Microsoft world relies on Azure Active Directory authentication tokens for access,” Wiz co-founder and chief technology officer Ami Luttwak said in a statement. “An attacker with an AAD signing key can access almost any app as any user, making it the most powerful attacker imaginable. This is a ‘shape shifter’ superpower.”
Microsoft revealed last week that token forgery techniques were exploited by Storm-0558 to extract unclassified data from victim mailboxes, but the exact profile of the cyberespionage operation remains unclear.
Windows makers said they are still investigating how the attackers obtained the MSA consumer signing keys. However, it is unknown whether this key acted as a master key to unlock data belonging to approximately 24 organizations.
Wiz’s analysis filled in some of the blanks, and the company found that “all Azure Personal Account v2.0 applications rely on the following list.” 8 public keysand all Azure multi-tenant v2.0 applications with Microsoft account enabled 7 public keys. ”
Additionally, it turned out that Microsoft replaced one of the public keys that were present in the list (thumbprint: “d4b4cccda9228624656bff33d8110955779632aa”). since at least 2016 That was somewhere between June 27, 2023 and July 5, 2023, about the same time period the company announced it had revoked its MSA keys.
“This led me to believe that the compromised keys obtained by Storm-0558 were also able to sign OpenID v2.0 tokens for multiple types of Azure Active Directory applications, even though they were private keys designed for Microsoft’s MSA tenant in Azure,” said Wiz.
Shielding Against Insider Threats: Mastering SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join us for this webinar to explore practical strategies and proactive security secrets using SaaS Security Posture Management.
“Storm-0558 appears to have managed to gain access to one of several keys intended for signing and validating AAD access tokens. The compromised key was trusted to sign OpenID v2.0 access tokens for individual accounts and mixed-viewer (multi-tenant or individual accounts) AAD applications.”
This effectively means that, in theory, a malicious attacker could forge access tokens for use with applications that rely on the Azure identity platform.
Even worse, the private key obtained could have been weaponized to forge tokens to authenticate as a user to affected applications that trust Microsoft OpenID v2.0 mixed audience and personal account certificates.
“An identity provider’s signing key is probably the strongest secret in the modern world,” said Wiz security researcher Shir Tamari. “Identity he provider his key gives him instant, single-hop access to everything from email boxes, files his services, cloud accounts, and more.”


