The operators behind the BazaCall callback phishing technique continue to evolve with the latest social engineering tactics to deploy malware on targeted networks.
The scheme ultimately serves as an entry point to carry out next-stage payload delivery for financial fraud, ransomware, cybersecurity firm Trellix, and more. Said In a report released last week.
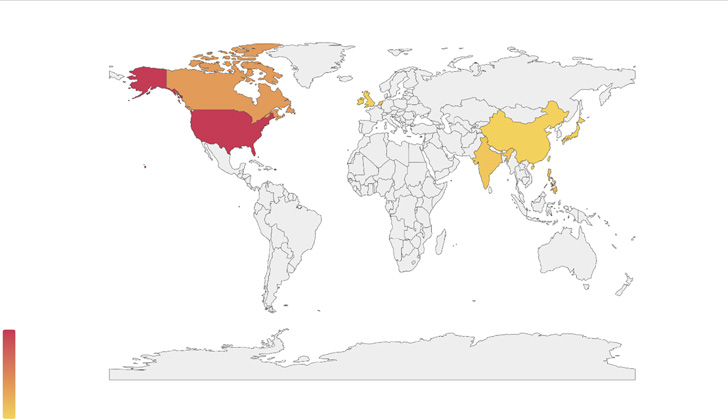
Key targets in latest attack wave include US, Canada, China, India, Japan, Taiwan, Philippines, UK
BazaCall, also known as BazarCall, was launched in 2020 with a novel approach of manipulating potential victims into distributing the BazarBackdoor (aka BazarLoader) malware by calling a phone number specified in a decoy email message. It became popular for the first time.
These email decoys are intended to notify recipients about renewals of trial subscriptions, such as antivirus services, and create a false sense of urgency. The message urges you to contact the support desk to cancel your plan. Otherwise, you risk being automatically charged for the premium version of the software.
The ultimate goal of the attack is to enable remote access to the endpoint under the guise of terminating a supposed subscription or installing a security solution to remove malware from the machine, thereby interfering with further activity. effectively pave the way.
Another tactic employed by operators is impersonating incident responders in PayPal-themed campaigns to trick callers into thinking their accounts were accessed from eight or more devices distributed in random locations around the world. That’s it.
Regardless of the scenario employed, the victim is asked to launch a specific URL. This is a specially crafted website designed to download and execute malicious executables, which along with other files also drops legitimate ScreenConnect remote desktop software.
After successful persistent access, the attacker opens a fake cancellation form asking the victim to enter personal information and sign in to their bank account to complete the refund, when they are actually tricked. Send money to scammers.
This development follows at least three different spin-off groups from the Conti ransomware cartel adopting callback phishing techniques as the initial intrusion vector for compromising corporate networks.
The bond with Conti doesn’t stop there. bazaar back dooris the creation of a cybercriminal group known as trick botwas taken over by Conti Earlier this year before the latter was shut down in May-June 2022 over its loyalty to Russia in its attack on Ukraine.




