Vice Society ransomware attackers have switched to yet another custom ransomware payload in recent attacks targeting different sectors.
“This ransomware variantPolyvice,” to implement a robust encryption scheme NTRU encryption When ChaCha20-Poly1305 algorithm, by Antonio Cocomazzi, SentinelOne Researcher Said in analysis.
The Vice Society, tracked by Microsoft under the name DEV-0832, is an intrusion, data breach, and extortion hacking group that first appeared in the threat landscape in May 2021.
Unlike other ransomware gangs, cybercriminals do not use in-house developed file-encrypting malware. Instead, third parties such as Hello Kitty, Zeppelin, and RedAlert ransomware have been known to deploy his lockers in their attacks.
According to SentinelOne, the threat actors behind the custom-branded ransomware are also selling similar payloads to other hacking teams based on PolyVice’s extensive similarities to ransomware strains Chily and SunnyDay. indicates that there is
This means a “Locker-as-a-Service” offered in the form of a builder by an unknown threat actor whose purchaser can specify the encrypted file extension, ransom note filename, ransom note You can customize the payload, including its contents. Above all, wallpaper text.
The shift from Zeppelin Finding weaknesses An encryption algorithm that allowed researchers at cybersecurity firm Unit221B to devise a decryption in February 2020.
Besides implementing a hybrid encryption scheme that combines asymmetric and symmetric encryption to securely encrypt files, PolyVice utilizes partial encryption and multi-threading to speed up the process.
As Cybereason revealed last week, it’s worth pointing out that the recently discovered Royal ransomware employs similar tactics to evade anti-malware defenses.
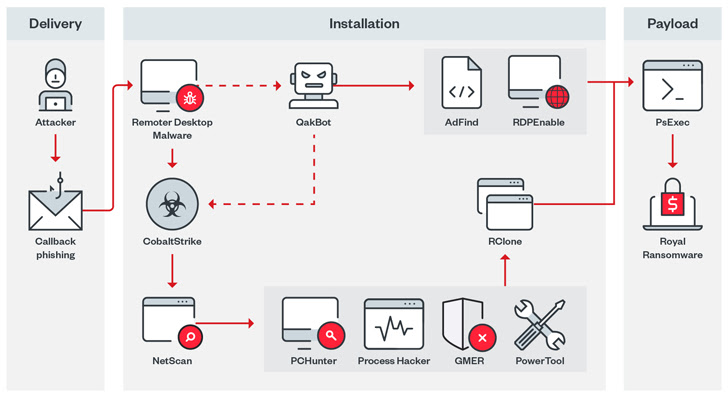
royalIt has its roots in the now-defunct Conti ransomware operation.
Leaked Conti Source Code Facilitates New Ransomware Variant
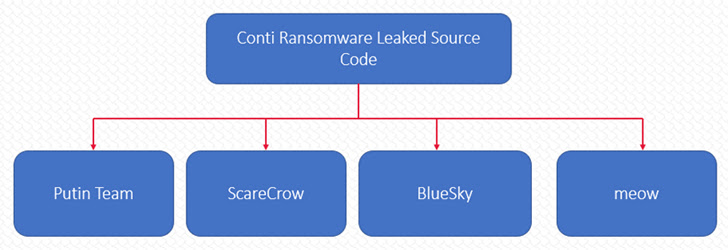
Meanwhile, the leak of Conti’s source code earlier this year spawned a slew of new ransomware, including Putin Team, ScareCrow, BlueSky, Meow, and Cyble. disclosedhighlighting how such leaks make it easier for threat actors to launch various derivatives with minimal investment.
“The ransomware ecosystem is constantly evolving, with a continuously expanding trend towards high levels of specialization and outsourcing,” Kokomazzi said, adding, “To enable the spread of advanced ransomware attacks, It poses a significant threat to the organization,” he added.



