Thousands of Citrix Application Delivery Controllers (ADC) and Gateway endpoints remain vulnerable to two critical security flaws that the company has disclosed over the past few months.
The problem at issue is CVE-2022-27510 When CVE-2022-27518 (CVSS score: 9.8), addressed by the virtualization service provider on Nov 8 and Dec 13, 2022 respectively.
CVE-2022-27510 is authentication bypass CVE-2022-27518 is a remote code execution bug that may allow hijacking of affected systems.
Citrix and the US National Security Agency (NSA) warned earlier this month that CVE-2022-27518 is being actively exploited by threat actors, including the APT5 National Assistance Group with ties to China.
Now, according to New analysis According to the NCC Group’s Fox-IT research team, thousands of Internet-connected Citrix servers are still unpatched, making them attractive targets for hacking crews.
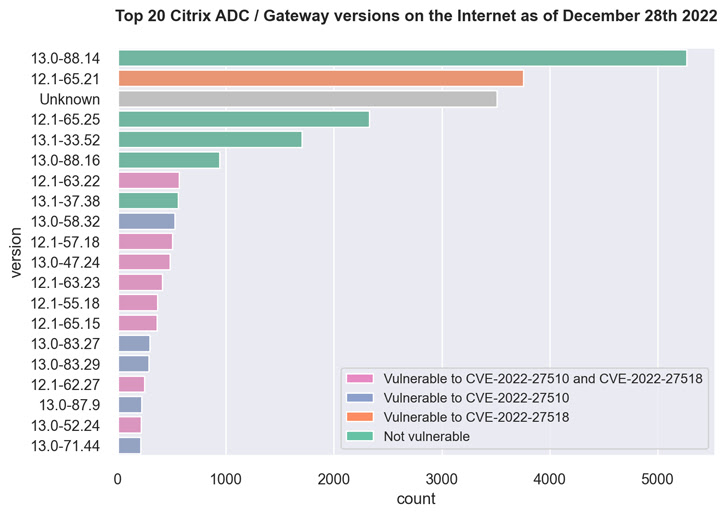
This includes over 3,500 Citrix ADC and Gateway servers running version 12.1-65.21 affected by CVE-2022-27518 and over 500 servers running 12.1-63.22 vulnerable to both flaws. will be
The majority of our 5,000+ servers are running 13.0-88.14, a version not affected by CVE-2022-27510 and CVE-2022-27518.
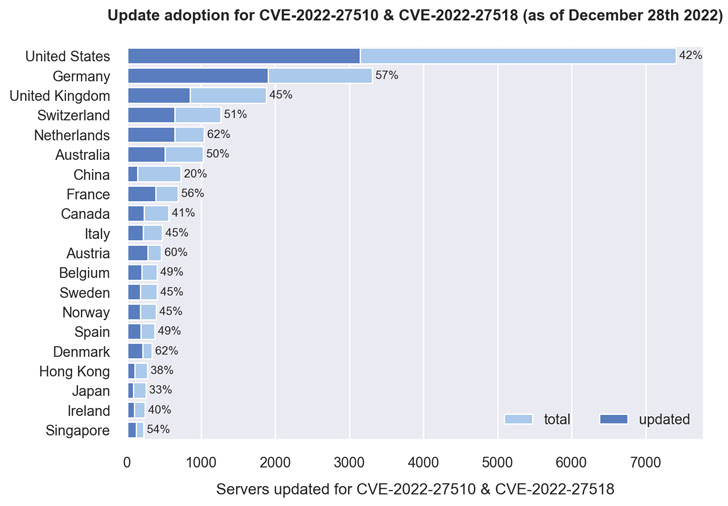
The country breakdown shows that over 40% of servers in Denmark, Netherlands, Austria, Germany, France, Singapore, Australia, UK, and US have been updated. About 550 servers have been patched.
Fox-IT version information Map from the MD5-like hash value present in the HTTP response of the login URL (i.e. “ns_gui/vpn/index.html”) to the respective version.



