A new open-source Remote Access Trojan (RAT) called Doge RAT It mainly targets Android users residing in India as part of an advanced malware campaign.
The malware is distributed through social media and messaging platforms under the guise of legitimate applications such as Opera Mini, OpenAI ChatGOT, and premium versions of YouTube, Netflix, and Instagram.
“Once installed on a victim’s device, the malware gains unauthorized access to sensitive data such as contacts, messages and banking credentials,” said cybersecurity firm CloudSEK. Said in Monday’s report.
“It can also take control of infected devices and enable malicious activities such as sending spam messages, fraudulent payments, modifying files, and even capturing photos remotely via the device’s camera. I have.”
DogeRAT, like many other malware-as-a-service (MaaS) products, was launched by an India-based developer through the Telegram channel, which has over 2,100 subscribers since it was created on June 9, 2022. being promoted.
This also includes a premium subscription priced at a very low price ($30) with additional features such as taking screenshots, stealing images, capturing clipboard contents, recording keystrokes, etc. increase.
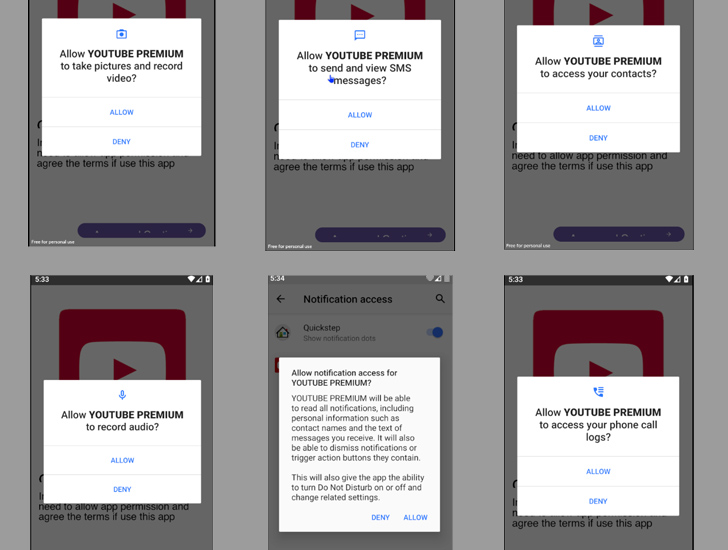
In a further attempt to make it more accessible to other criminals, a free version of DogeRAT was published on GitHub, along with screenshots and video tutorials demonstrating its functionality.
“We do not endorse any illegal or unethical use of this tool,” the developer says in the repository’s README.md file. “User assumes all responsibility for the use of this software.”
Upon installation, the Java-based malware requests an intrusion permission to perform data collection purposes before infiltrating the Telegram bot.
Zero Trust + Deception: Learn How to Outsmart Attackers!
See how Deception can detect advanced threats, stop lateral movement, and strengthen your Zero Trust strategy. Join us for an insightful webinar!
CloudSEK researcher Anshuman Das said, “This campaign is a stark reminder of the financial motivation of scammers to continually evolve their tactics.”
“They are not limited to creating phishing websites, but also distributing modified RATs and reusing malicious apps to run low-cost, easy-to-set-up yet highly lucrative fraudulent campaigns. You can also.”
The discovery comes as Google-owned Mandiant details a new Android backdoor called LEMONJUICE designed to allow remote control and access of compromised devices.
“This malware can track device location, record microphone, retrieve contact list, access calls, SMS, clipboard, notification logs, view installed applications, download and upload files, and monitor connection status. It is possible to view and execute additional commands from the C2 server.” Researcher Jared Wilson Said.
In a related development, Doctor Web revealed: 100+ apps It contains a spyware component called SpinOk and has been downloaded over 421 million times in total via the Google Play store.
of moduleis distributed as a marketing software development kit (SDK) designed to collect sensitive information stored on the device and copy and replace clipboard contents.
Some of the most popular apps found to contain the SpinOk Trojan include Noizz, Zapya, VFly, MVBit, Biugo, Crazy Drop, Cashzine, Fizzo Novel, CashEM and Tick.


