Details about a currently patched security flaw in the Windows Common Log File System (CLFS) have emerged. This could be exploited by an attacker to gain elevated permissions on a compromised machine.
This issue, tracked as CVE-2022-37969 (CVSS score: 7.8), was addressed by Microsoft as part of the September 2022 Patch Monthly Update, but is being actively exploited in the wild. has also been pointed out.
“The attacker must already have access to the target system and the ability to execute code.” I got it on that recommendation. “This technique does not allow remote code execution if an attacker does not already have that capability on the targeted system.”
We also acknowledge that CrowdStrike, DBAPPSecurity, Mandiant, and Zscaler researchers reported the vulnerability without delving into additional details about the nature of the attack.
Currently, the Zscaler ThreatLabz research team: disclosed On September 2nd, 2022, we confirmed that we had captured the zero-day publicly available exploit at the time.
“The vulnerability is due to a lack of strict bounds checking on the field cbSymbolZone in the base record header of the base log file (BLF) of CLFS.sys,” the cybersecurity firm told HackerNews.
“If field cbSymbolZone is set to an invalid offset, out-of-bounds write Occurs at invalid offsets. ”
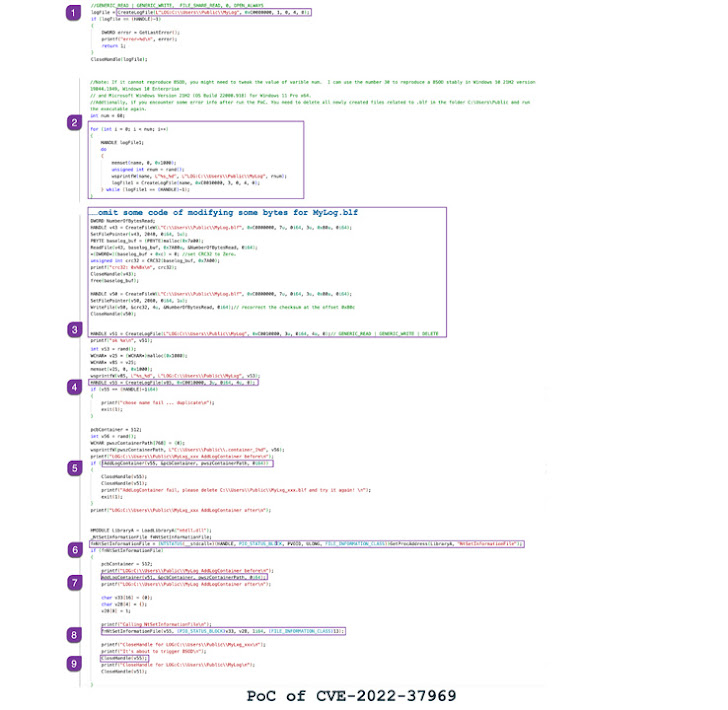
CLFS is Generic logging service It can be used by software applications running in both user mode or kernel mode to record data and events and optimize log access.
Use cases related to CLFS include online transaction processing (OLTP), network event logs, compliance audits, and threat analysis.
According to Zscaler, the vulnerability is rooted in a metadata block called the base record. base log fileIt is generated when a log file is created using the CreateLogFile() function.
“[Base record] including Symbol table Stores information about various clients, containers, and security contexts associated with the base log file, as well as accounting information about these.” Alex IonescuChief Architect of Crowdstrike.
As a result, successful exploitation of CVE-2022-37969 via a specially crafted base log file can lead to memory corruption and even system crashes (Blue Screen of Death or Blue Screen of Death). BSoD) in a reliable manner.
However, system crashes are just one of the consequences of exploiting vulnerabilities. It can also be weaponized to achieve privilege escalation.
Zscaler has also made available a proof-of-concept (PoC) procedure that triggers the security hole. This makes it imperative for Windows users to upgrade to the latest version to mitigate potential threats.




