North Korea related scar craft The group has been attributed to a previously undocumented backdoor. Dolphin Used by threat actors against targets in their southern counterparts.
“Back door […] It has a wide range of spying capabilities such as monitoring drives and portable devices, extracting files of interest, taking keylogging and screenshots, stealing credentials from browsers,” said Filip Jurčacko, a researcher at ESET. says. Said In a new report released today.
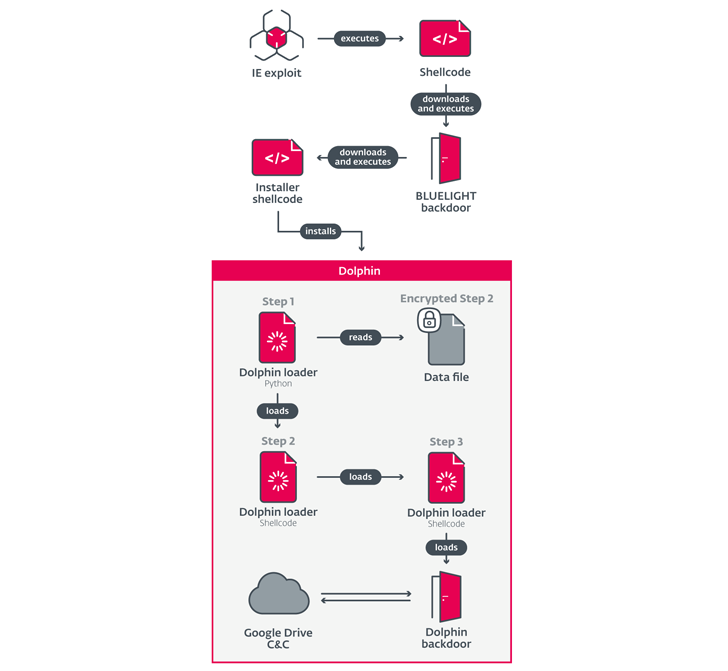
Dolphin is said to be selectively deployed. The malware uses cloud services such as Google Drive for data extraction and command and control.
A Slovak cybersecurity firm said it discovered the implant was deployed as a final-stage payload as part of a watering hole attack directed at a South Korean digital newspaper in early 2021.
Campaign first discovered by Kaspersky At last year’s Volexity, two flaws in Internet Explorer (CVE-2020-1380 When CVE-2021-26411) drops a backdoor named BLUELIGHT.
ScarCruft, also known as APT37, InkySquid, Reaper and Ricochet Chollima, is a geopolitically motivated APT group with a track record of attacking government agencies, diplomats and media outlets related to North Korea issues. Known to be active since at least 2012.
Earlier this April, cybersecurity firm Stairwell launched a spear-phishing attack targeting journalists covering the country, with the ultimate goal of deploying malware dubbed GOLDBACKDOOR, which duplicates another ScarCruft backdoor, BLUELIGHT. clarified the details.
ESET’s latest findings shed light on a second, more sophisticated backdoor delivered to a small pool of victims via BLUELIGHT, demonstrating highly targeted espionage .
This is accomplished by running an installer shellcode that launches a loader consisting of Python and shellcode components. The latter runs another shellcode loader to drop the backdoor.
“While the BLUELIGHT backdoor performs basic reconnaissance and post-breach machine assessment, Dolphin is more sophisticated and is manually deployed only to selected victims,” explained Jurčacko. To do.
What makes Dolphin so much more powerful than BLUELIGHT is its ability to search removable devices and steal files of interest such as media, documents, emails and certificates.
Since it was first discovered in April 2021, the backdoor has reportedly been iterated three times in a row, with its own set of improvements, giving it more ability to evade detection. .
“Dolphin is the latest addition to our extensive arsenal of backdoors that exploit ScarCruft’s cloud storage service,” said Jurčacko. “One of his unusual features found in previous versions of the backdoor is the ability to change the victim’s settings on her Google and her Gmail accounts to reduce their security. This is to maintain access to her account.”



