The developers behind the Brave open source web browser have revealed a new privacy-preserving system called the Data Query and Search System. Frodo PIR.
idea, company Saidsecure browsing, checking passwords against compromised databases, certificate revocation checking, and using the technology to build a wide range of use cases such as streaming.
the scheme is called Frodo PIR Because “clients can run hidden queries against the server in the same way that Frodo remained hidden from Sauron”, oJ. RR Tolkiens Lord of the Ring.
PIR, abbreviated Search for personal informationis a cryptographic protocol that allows a user (aka client) to retrieve information from a database server without revealing to its owner which elements were selected.
In other words, the goal is to provide information (e.g. cooking videos) to the Platform without the Service Provider inferring it from a user’s search history to provide personalized recommendations or targeted advertisements based on their search criteria. to be able to query
One way to achieve this is by using the following approach. homomorphic encryptionThis allows computations to be performed directly on the encrypted data without requiring access to the private key.
However, the general problem plaguing such methods is that they are “expensive, either in terms of bandwidth or the time it takes to process each client query”, making practical deployment impossible. is.
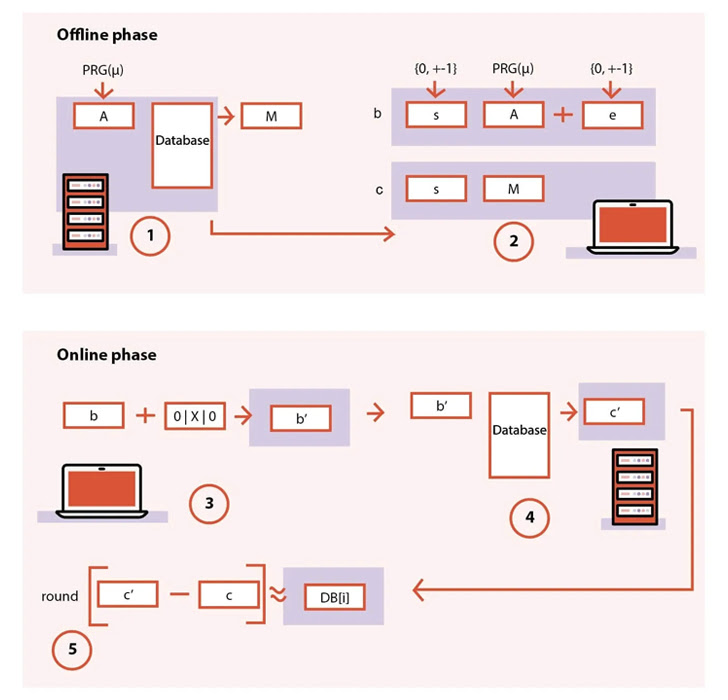
This is where FrodoPIR intervenes. This includes his two phases, an offline preparation step and an online step where the client sends encrypted queries to the server.
The server then chooses to return a positive or negative value depending on whether the query was found in the database without knowing what the user was actually querying.
“In terms of database performance with 1 million KB elements, FrodoPIR takes less than 1 second to respond to client queries, with an expansion factor of over 3.6x for server response sizes, and a financial It costs ~$1. Said In the project’s GitHub description.
Two Google Open Source Privacy Enhancing Technologies (PET)
Development comes as Google Said As part of our ongoing effort to democratize access to technology beyond that, we are open sourcing two privacy-enhancing technologies (PETs). federated learning When Differential privacy.
It consists of a new machine learning tool called Magritte It is designed to blur objects such as license plates that appear in videos and uses fully homomorphic encryption (FHE) Transpiler.
of Transpileraka source-to-source compilers or translators, are designed to perform computation-based queries over encrypted information without access to personally identifiable data.
PETs “offer new ways for the broader developer community (researchers, governments, nonprofits, businesses, etc.) to deploy and enhance privacy features in their own work,” Google said. I’m here.



