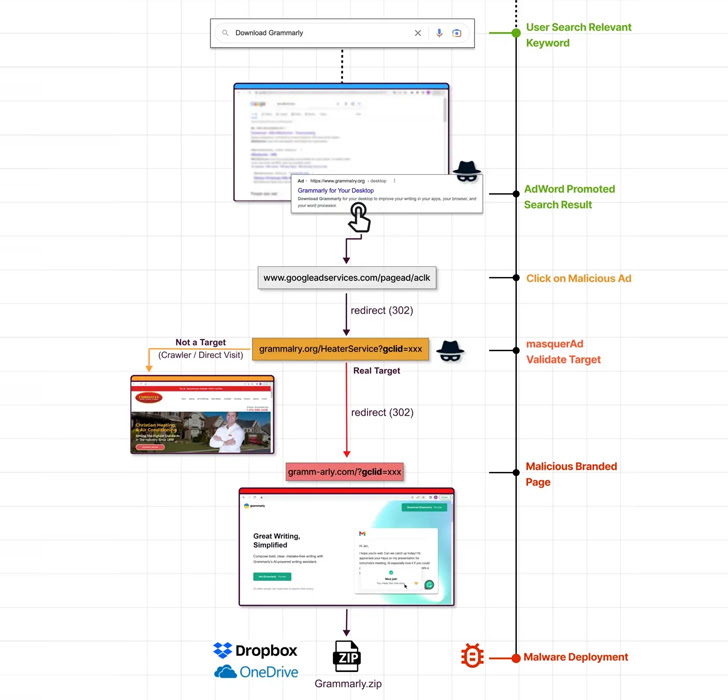
Users searching for popular software are being targeted in new malvertising campaigns that abuse Google ads to deliver trojanized variants that deploy malware such as Raccoon Stealer and Vidar. increase.
The campaign relies on seemingly trustworthy websites with typosquatted domain names that appear at the top of Google search results in the form of malicious ads by hijacking searches for specific keywords. increase.
The ultimate goal of such attacks is pull the wool over eyes no doubt user For downloading malicious programs and potentially unwanted applications.
In one campaign published by Guardio Labs, the attackers created a network of benign sites that were promoted on search engines. Clicking on the site redirects visitors to a phishing page containing a trojanized ZIP archive of him hosted on Dropbox or OneDrive.
“The moment these ‘fake’ sites are visited by a targeted visitor (the one who actually clicked on the promoted search result), the server immediately redirects them to the fraudulent site, from which the malicious It redirects to a payload with a Said.
Camouflaged software includes AnyDesk, Dashlane, Grammarly, Malwarebytes, Microsoft Visual Studio, MSI Afterburner, Slack, and Zoom.
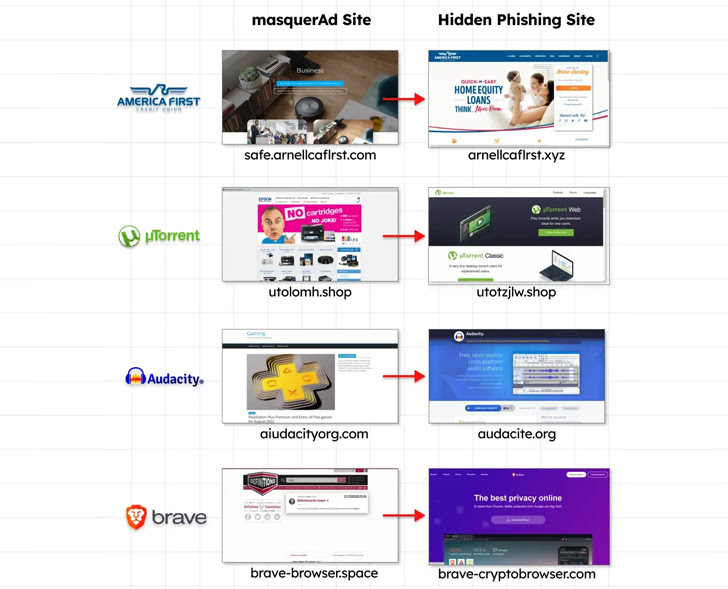
Guardio Labs, which dubbed the campaign MasquerAds, believes it came from a threat actor it tracks under the name Vermux, who “abuses a huge number of brands and continues to evolve.”
The Vermux operation singled out users primarily in Canada and the United States, using masquerAds sites tailored to search for AnyDesk and MSI Afterburner to proliferate cryptocurrency miners and Vidar information stealers.
This development shows the continued use of typosquatted domains that mimic legitimate software to lure users into installing malicious software. android When Windows app.
It’s also not the first time the Google Ads platform has been used to deliver malware. Last month, Microsoft unveiled an attack campaign it uses to deploy his BATLOADER using advertising services to drop the Royal ransomware.
Besides BATLOADER, malicious actors also use malvertising techniques to distribute IcedID malware through clone web pages of well-known applications such as Adobe, Brave, Discord, LibreOffice, Mozilla Thunderbird, TeamViewer, etc. .
“IcedID is a notable malware family that can deliver other payloads, including Cobalt Strike and other malware,” said Trend Micro. Said last week. “IcedID allows attackers to carry out highly impactful follow-through attacks that lead to system-wide compromise, such as data theft and ransomware subversion.”
Findings are also provided by the US Federal Bureau of Investigation (FBI). warned “Cybercriminals are using search engine advertising services to impersonate brands, direct users to malicious sites that host ransomware, and steal login credentials and other financial information.”



