Portuguese users targeted by new codenamed malware crypto clippy You can steal cryptocurrencies as part of a malvertising campaign.
This activity utilizes SEO poisoning techniques to direct users searching for “WhatsApp Web” to malicious domains that host malware. Palo Alto Networks Unit 42 Said In a new report released today.
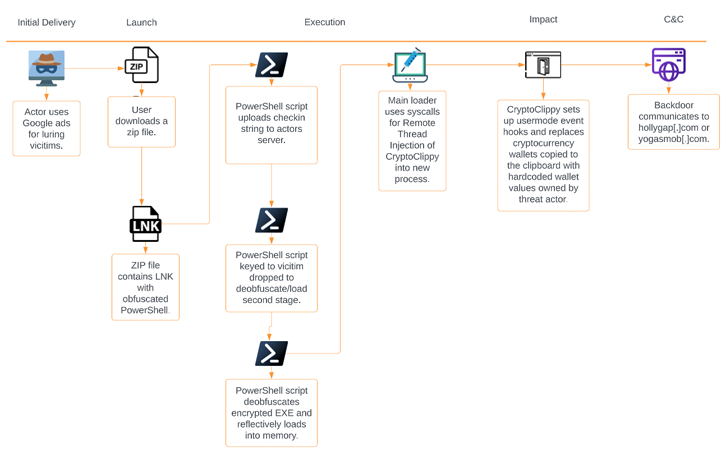
CryptoClippy, a C-based executable, is a type of cryware known as clipper malware that monitors a victim’s clipboard for content that matches cryptocurrency addresses, allowing it to access wallets under the attacker’s control. Replace with your address.
According to Unit 42 researchers, “Clipper malware uses regular expressions (regexes) to identify the type of cryptocurrency an address is associated with.
“We then replace the clipboard entry with a visually similar but appropriate attacker-controlled cryptocurrency wallet address. Then you actually send the cryptocurrency directly to the attacker.”
This illegal scheme is estimated to have brought in around $983 in profits so far, and victims have been found across the manufacturing, IT services, and real estate industries.
It is worth noting that the actors associated with GootLoader employ tainted search results to deliver malware. malware.
Learn How to Secure Your Identity Perimeter – A Proven Strategy
Improve your business security in our upcoming expert-led cybersecurity webinar: Exploring Identity Perimeter Strategies!
Another approach used to determine suitable targets is the Traffic Direction System (TDS). It checks if the preferred browser language is Portuguese and if it is, it directs the user to a fraudulent landing page.
Users who do not meet the required criteria are redirected to the legitimate WhatsApp web domain without further malicious activity, thus avoiding detection.
According to the findings, SecurityScorecard Luma It can collect data from web browsers, cryptocurrency wallets, and various apps such as AnyDesk, FileZilla, KeePass, Steam, and Telegram.


