Codename of new phishing campaign Multi# Storm targeted India and the United States by leveraging JavaScript files to deliver remote access Trojans to compromised systems.
According to Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov, “The attack chain consists of a victim’s machine running multiple unique RAT (remote access Trojan) malware instances, such as Warzone RAT and Quasar RAT. end by infecting the Said.
“Both are used for command and control at various stages of the infection chain.”
A multi-step attack chain is initiated when an email recipient clicks an embedded link pointing to a password-protected ZIP file (“REQUEST.zip”) with password “12345” hosted on Microsoft OneDrive .
Extracting the archive file reveals a highly obfuscated JavaScript file (“REQUEST.js”). Double-clicking on this file activates the infection by executing two PowerShell commands that retrieve and execute two separate payloads from OneDrive.
The first of the two files is a decoy PDF document that is displayed to the victim, while the second file, a Python-based executable, runs covertly in the background.
This binary acts as a dropper that extracts and executes the main payload packed inside in the form of a Base64-encoded string (“Storm.exe”), but changes persistence to the Windows registry. It doesn’t work before you set it.
The binary also decodes a second ZIP file (“files.zip”). This he contains 4 different files, each designed to bypass User Account Control (UAC), create mock trusted directories and elevate privileges.
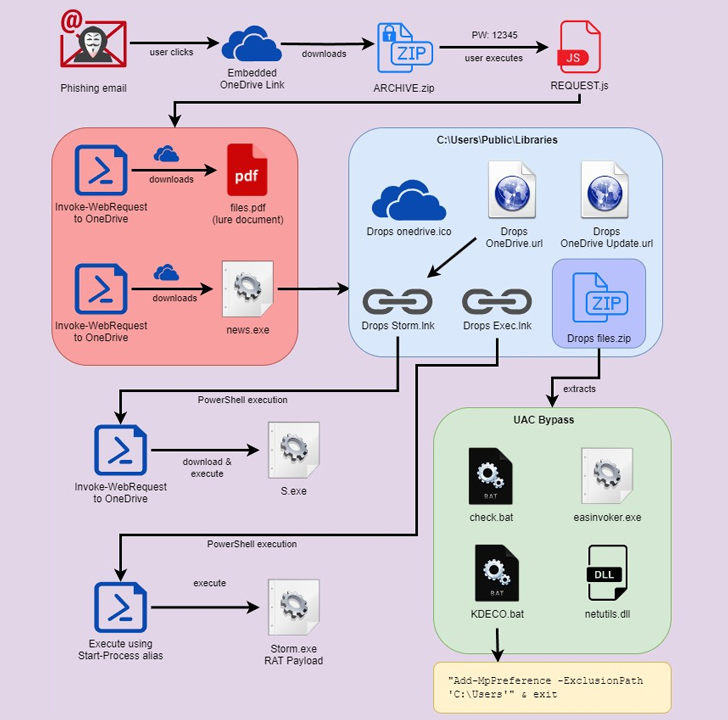
Inside the file is a batch file (“check.bat”), which Securonix says has some things in common with another loader called DBatLoader, despite the different programming languages used. That’s what I mean.
A second file named “KDECO.bat” runs a PowerShell command to tell Microsoft Defender Antivirus exclusion rule Skip the “C:\Users” directory.
The attack culminates in the deployment of Warzone RAT (aka Ave Maria), an off-the-shelf malware that sells for $38/month. The malware comes with an exhaustive list of functions to collect sensitive data and download additional malware such as the Quasar RAT. .
“It’s important to remain vigilant, especially when it comes to phishing emails, especially when the sense of urgency is emphasized,” the researchers said.
“This particular temptation was generally less noticeable because it required the user to run the JavaScript file directly. Shortcut files and files with double extensions seemed to have a higher success rate. increase.”



