A threat activity cluster under development was discovered using Google Ads in one of its campaigns to distribute various post-compromise payloads. royal ransomware.
Discovering an updated malware delivery method in late October 2022, Microsoft tracks this group under the name: DEV-0569.
“Observed DEV-0569 attacks show a pattern of continued innovation, with new detection techniques, defense evasion, and various post-compromise payloads being regularly incorporated, increasing the facilitation of ransomware. ,” said the Microsoft Security Threat Intelligence team. Said in analysis.
This threat actor is known to use malvertising to lure unsuspecting victims to malware downloader links masquerading as software installers for legitimate apps such as Adobe Flash Player, AnyDesk, LogMeIn, Microsoft Teams, and Zoom. I’m here.
A malware downloader called BATLOADER is a dropper that acts as a pipe to distribute the next stage payload. It has been observed sharing overlaps with another malware called ZLoader.
BATLOADER RECENT ANALYSIS BY eSentire When VMware Using search engine optimization (SEO) poisoning to entice users to download malware from compromised websites or attacker-created domains, as well as pointing out malware’s stealthiness and persistence Did.
Alternatively, phishing links are shared through spam emails, fake forum pages, blog comments, and even contact forms on the targeted organization’s website.
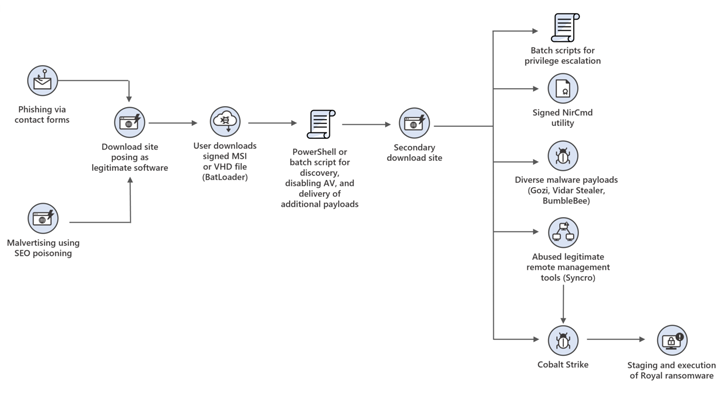
“DEV-0569 used a variety of infection chains using PowerShell and batch scripts, ultimately ending up with malware such as information stealers and legitimate remote administration tools used for persistence on the network. It led to a payload download,” notes the tech giant.
“Management tools also provide access points for staging and spreading ransomware.”
It also uses a tool called NSudo to launch programs with elevated privileges and add registry values designed to disable antivirus solutions to weaken your defenses.
Using Google Ads to selectively deliver BATLOADER demonstrates the diversification of DEV-0569’s distribution vector, allowing it to reach more targets and deliver its malware payload. the company points out.
Additionally, it joins malware such as Emotet, IcedID, and Qakbot, positioning the group to act as an initial access broker for other ransomware operations.
“Because DEV-0569’s phishing schemes exploit legitimate services, organizations are leveraging mail flow rules to catch suspicious keywords and apply broad exceptions, such as those associated with IP range or domain-level allowlists. You can also check the


