On the second Tuesday of each month, Microsoft released another security update that fixes 97 total defects It affects that software, one of which is being actively exploited in real-world ransomware attacks.
Of the 97 bugs, 7 are rated Critical and 90 are rated Important. Interestingly, 45 of the flaws are remote code execution flaws, followed by privilege escalation vulnerabilities at 20. This update also follows fixes for 26 vulnerabilities in the Edge browser released over the past month.
The security flaws being actively exploited are: CVE-2023-28252 (CVSS score: 7.8), a privilege escalation bug in the Windows Common Log File System (CLFS) driver.
In an advisory, Microsoft said, “An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” and credits researchers Boris Larin, Genwei Jiang, and Quan Jin for reporting the issue. I admit it.
CVE-2023-28252 is CVE-2022-24521, CVE-2022-37969, and CVE-2023-23376 (CVSS score: 7.8 ). At least 32 vulnerabilities have been identified in CLFS since 2018.
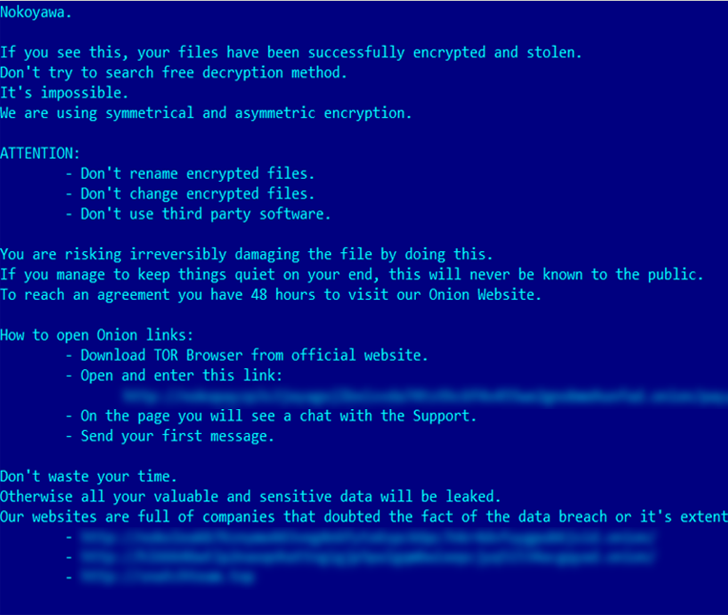
According to Russian cybersecurity firm Kaspersky, the vulnerability has been weaponized by cybercriminal groups deploying the Nokoyawa ransomware against small businesses in the Middle East, North America, and Asia.
“CVE-2023-28252 is an out-of-bounds write (increment) vulnerability that can be exploited when the system attempts to extend a metadata block,” Larin said. Said“This vulnerability is triggered by manipulation of the base log file.”
In light of the ongoing exploitation of the flaw, CISA will: Added List Windows zero-days in the Catalog of Known Exploited Vulnerabilities (KEV), which mandates agencies of the Federal Civil Administration (FCEB) to secure the system by May 2, 2023.
Also patched are critical remote code execution flaws affecting the DHCP Server service, Layer 2 Tunneling Protocol, Raw Image Extension, Windows Point-to-Point Tunneling Protocol, Windows Pragmatic General Multicast, and Microsoft Message Queuing. increase (MSMQ).
MSMQ bug tracked as CVE-2023-21554 (CVSS score: 9.8), called QueueJumper by Check Point, can lead to the execution of malicious code and take over the MSMQ server by sending specially crafted malicious MSMQ packets to it .
“The CVE-2023-21554 vulnerability could allow an attacker to reach on TCP port 1801 and execute code remotely without authentication,” said Check Point researcher Haifei Li. Said“In other words, an attacker could use an exploit to gain control of the process via a single packet to the 1801/tcp port and trigger the vulnerability.”
Two other flaws found in MSMQ CVE-2023-21769 and CVE-2023-28302 (CVSS score: 7.5), service crashes and Windows Blue Screen of Death (BSoD).
Learn How to Secure Your Identity Perimeter – A Proven Strategy
Improve your business security in our upcoming expert-led cybersecurity webinar: Exploring Identity Perimeter Strategies!
Microsoft has also updated the advisory. CVE-2013-390010-year-old WinVerifyTrust Signature Verification Vulnerability, including Server Core installed versions of –
- Windows Server 2008 Service Pack 2 for 32-bit systems
- Windows Server 2008 Service Pack 2 for x65-based Systems
- Windows Server 2008 R2 Service 1 for x64-based Systems
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019, and
- Windows Server 2022
This development is based on observations that North Korea-related attackers have used this flaw to embed encrypted shellcode into legitimate libraries without disabling Microsoft-issued signatures. was broken.
Microsoft Issues Guidance on BlackLotus Bootkit Attack
Alongside the update, the tech giant also issued the following guidance: CVE-2022-21894 (aka Baton Drop) is a now-fixed Secure Boot Bypass flaw exploited by threat actors that use an early Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus to establish persistence on the host. is.
Some indicators of compromise (IoCs) include the EFI system partition (ESP), Microsoft Defender Antivirus stopped, presence of staging directory ESP:/system32/, and changes to registry key HKLM:\SYSTEM\CurrentControlSet\Control\DeviceGuard\Scenarios\HypervisorEnforcedCodeIntegrity.
“UEFI bootkits are particularly dangerous because they run when the computer boots, before the operating system is loaded. As such, they can interfere with or defeat various operating system (OS) security mechanisms. There is,” said the Microsoft Incident Response team. Said.
Microsoft will also remove compromised devices from its network, examine evidence of subsequent activity, reformat or restore machines from known clean backups that include EFI partitions, and maintain credential hygiene. and apply the principle of least privilege (PoLP).
Software patches from other vendors
In addition to Microsoft, other vendors have also released security updates over the past few weeks to fix several vulnerabilities, including:


