An unknown cryptocurrency exchange in Japan was targeted earlier this month by a new attack that introduced an Apple macOS backdoor called JokerSpy.
We monitor an intrusion set under the name Elastic Security Labs. REF9134, Said The attack installed Swiftbelt. This is a Swift-based enumeration tool inspired by an open-source utility called Swiftbelt. Seat belt.
JokerSky was first documented last week by Bitdefender, described as a sophisticated toolkit designed to compromise macOS machines.
As for the attackers behind the attack, the fact that the attack utilizes a series of programs written in Python and Swift, with the ability to collect data and execute arbitrary commands on the compromised host. Other than that, I know very little.
The main component of the toolkit is a self-signed multi-architecture binary known as xcc designed to check FullDiskAccess and ScreenRecording permissions.
The file is signed as XProtectCheck, indicating an attempt to impersonate it as XProtectCheck. X protectthe antivirus technology built into macOS that utilizes signature-based detection rules to remove malware from already infected hosts.
In an incident analyzed by Elastic, following xcc creation, the threat actor “attempts to bypass TCC privileges by creating its own xcc.” TCC database I’m trying to replace an existing one. ”
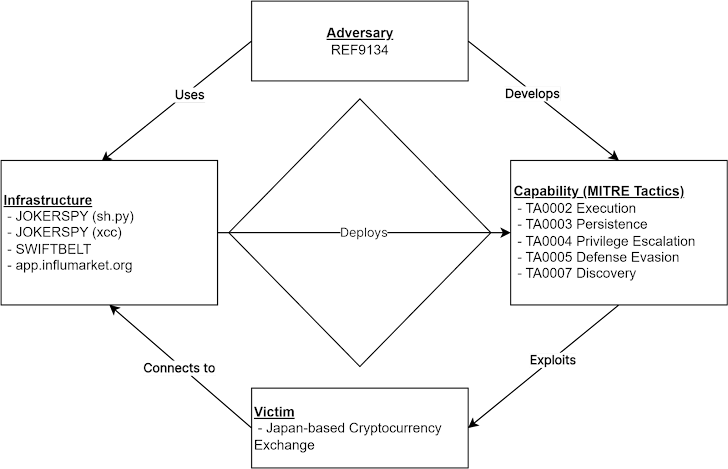
“On June 1st, a new Python-based tool was seen running from the same directory as xcc and was used to run an open-source macOS post-exploit enumeration tool known as Swiftbelt,” said a security researcher. said Colson Wilhoit, Salim Bitam and Seth Goodwin of said Andrew Pease and Ricardo Ungleanu.
The attack targeted a major Japan-based cryptocurrency service provider that focuses on asset exchanges for trading Bitcoin, Ethereum, and other popular cryptocurrencies. The name of the company was not disclosed.
The xcc binaries are launched by Bash through three different apps named IntelliJ IDEA, iTerm (a terminal emulator for macOS), and Visual Studio Code. This indicates that a backdoor version of the software development software may be in use. Get initial access.
Another notable module installed as part of the attack is sh.py. This is a Python implant used as a conduit for delivering other post-exploitation tools such as Swiftbelt.
“Unlike other enumeration techniques, Swiftbelt calls Swift code to avoid creating command line artifacts,” the researchers said. “Notably, the xcc variant is also written using Swift.”




