Google announced the availability of open source on Tuesday OSV scannera scanner intended to provide easy access to vulnerability information on various projects.
of Go-based toolsopen source vulnerabilities (OSVs.
“OSV-Scanner produces reliable, high-quality vulnerability information, bridging the gap between the developer’s package list and the information in the vulnerability database,” Pan added.
The idea is to identify all transitive dependencies of your project and highlight the related vulnerabilities using data pulled from the OSV.dev database.
Google further states that the open source platform supports 16 ecosystems, including all major languages, Linux distributions (Debian and Alpine), Android, the Linux kernel, and OSS-Fuzz.
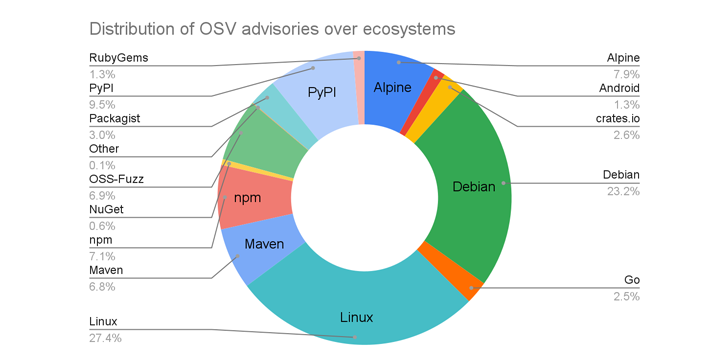
As a result of this expansion, OSV.dev has gone from 15,000 security alerts a year ago to 38,000 using Linux (27.4%), Debian (23.2%), PyPI (9.5%) and Alpine (7.9%). This is the repository for the above advisories. %), with npm (7.1%) occupying the top 5 slots.
As a next step, the internet giant will build in support for C/C++ flaws by building a “high-quality database” that includes “adding accurate commit-level metadata to CVEs.” said it was working.
\
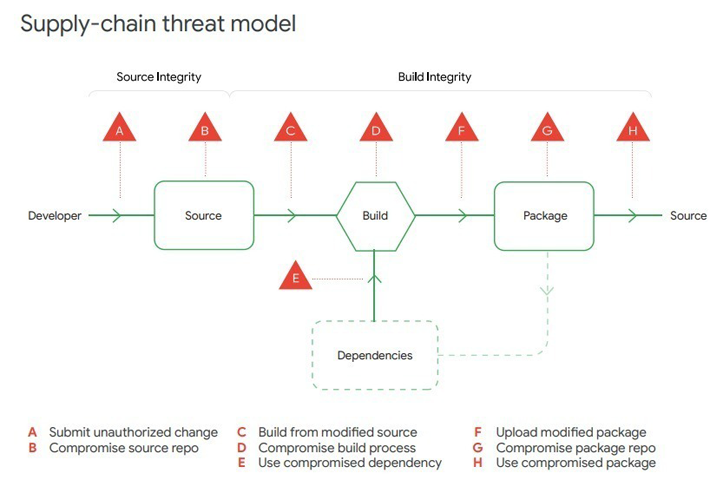
OSV-Scanner arrives almost two months after Google launched GUAC (short for Graph for Understanding Artifact Composition) to complement the supply chain level of software artifacts (SLSA or “salsa”) was part of an effort to strengthen the security of the software supply chain.
Last week, Google announced a new “Security PerspectiveIt reports calling on organizations to develop and deploy a common SLSA framework to prevent tampering. improve completenessto protect your packages from potential threats.
Other recommendations provided by the company include taking additional open source security responsibilities and adopting a more holistic approach to address risks such as those posed by the Log4j vulnerability and the recent SolarWinds incident. will be
“Attacks on the software supply chain typically require strong technical aptitude and a long-term commitment to success,” the company said. “Sophisticated attackers are more likely to have both the intent and the ability to carry out this type of attack.”
“Most organizations are vulnerable to software supply chain attacks. Attackers take the time to target third-party providers that have trusted connections to customer networks. , deep into the network of the ultimate target.”



