Two long-running surveillance campaigns targeting Uyghur communities in China and elsewhere have been discovered using Android spyware tools designed to gather sensitive information and track their whereabouts.
This includes a previously undocumented variant of the malware called BadBazaar and an updated variant of the spying artifact called “BadBazaar”. moonshine It was announced in September 2019 by researchers at the University of Toronto’s Citizen Lab.
“Mobile surveillance tools such as BadBazaar and MOONSHINE can be used to track many ‘pre-criminal’ activities and behaviors that Xinjiang authorities deem indicative of religious extremism and separatism,” said Lookout. Said A detailed write-up of the operation.
According to the security firm, the BadBazaar campaign is said to date back to late 2018 and consists of 111 unique apps masquerading as benign video players, messengers, religious apps, and even TikTok.
While these samples were distributed through Uyghur social media platforms and communication channels, Lookout noted that they discovered a dictionary app named “Uyghur Lughat” in the Apple App Store. This app collects basic iPhone information by communicating with the servers used by corresponding Androids.
iOS app Continue It will be available on the App Store.
“BadBazaar variants often gain their surveillance capabilities by downloading updates from websites, [command-and-control server]Attackers may wish to update their iOS samples later with similar monitoring capabilities,” the researchers noted.
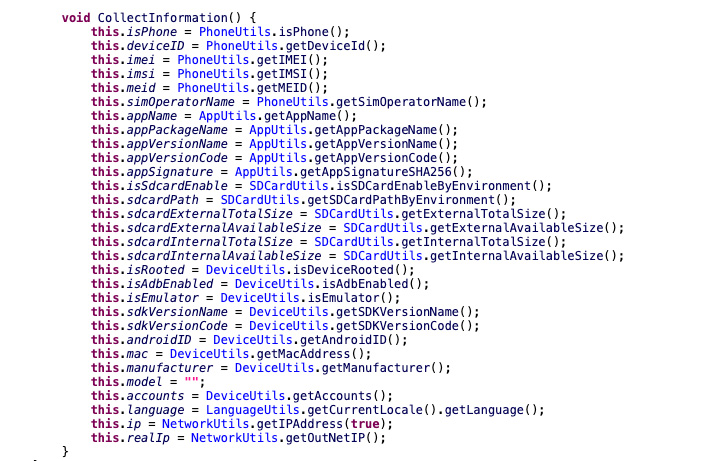
Once installed, BadBazaar comes with several features that allow you to collect call logs, GPS locations, SMS messages and files of interest. Record phone calls; take pictures; steal tons of device metadata.
Further analysis of BadBazaar’s infrastructure revealed overlaps with another spyware campaign targeting ethnic minorities that was uncovered in July 2020. double agent.
Similarly, MOONSHINE-powered attacks have seen more than 50 malicious apps designed to collect personal data, record audio and download arbitrary files from infected devices since July 2022. used.
“The majority of these samples are trojanized versions of popular social media platforms such as WhatsApp and Telegram, or trojanized Islamic cultural apps, Uyghur language tools, or prayer apps. version,” said the researchers.
Previous malicious cyber activity utilizing the MOONSHINE Android spyware kit was by a threat actor tracked as POISON CARP (aka Evil Eye or Earth Empusa). This threat actor is a China-based nation-state group known for its attacks against Uyghurs.
Asked for comment, Google said that all Android apps are Google Play Protect Regularly monitor app behavior to identify policy violations before they are published on the app’s storefront.
“as App Defense Alliance PartnerWe regularly work with Lookout and others to keep Google Play safe,” the tech giant told The Hacker News. review process. “
The findings come a month after Check Point disclosed details of another long-running surveillanceware operation targeting the Turkic Muslim community that deployed a Trojan named MobileOrder from at least 2015. It’s after the rest.
“These new variants of BadBazaar and MOONSHINE add to an already extensive collection of proprietary surveillance wear used in campaigns to monitor and subsequently detain individuals in China,” Lookout said.
“Both BadBazaar and MOONSHINE are widely distributed, and the speed at which new features are introduced indicates ongoing development of these families and continued demand for these tools.”
The development also follows a report from Google Project Zero last week. It’s been found Evidence of an unnamed commercial surveillance vendor weaponizing three zero-day security flaws in Samsung phones with Exynos chips running kernel version 4.14.113.the security hole is plugged in By Samsung in March 2021.
That said, the exploitation reflects a pattern similar to recent breaches where malicious Android apps were exploited to target users in Italy and Kazakhstan, using an implant called Hermit associated with Italian company RCS Lab. says the search giant.



