Attackers behind Windows banking malware known as Casbaneiro It is believed to be behind a new Android Trojan called . Bradex This has been observed targeting users in Brazil as part of an ongoing multi-platform campaign.
BrasDex describes a “complex keylogging system and sophisticated automatic transfer system (ATS) designed to exploit accessibility services to extract credentials from a set of apps specifically targeting Brazil. It features an engine. Said In a report released last week.
The Dutch security firm said the command and control (C2) infrastructure used in conjunction with BrasDex was also used for control. Casbaneiroknown to attack banks and cryptocurrency services in Brazil and Mexico.
A hybrid Android and Windows malware campaign is estimated to have caused thousands of infections so far.
Disguised as a Banco Santander banking app, BrasDex abuses Android’s accessibility APIs to record keystrokes typed by victims, moving away from traditional methods of overlay attacks to steal credentials and other personal data. It is also a symbol of trends.
It is also designed to obtain account balance information, after which it hijacks the infected device and programmatically initiates fraudulent transactions.
Another notable thing about BrasDex is its focus on the PIX payment platform. It allows a Brazilian bank customer to send money simply by using his email address or phone number.
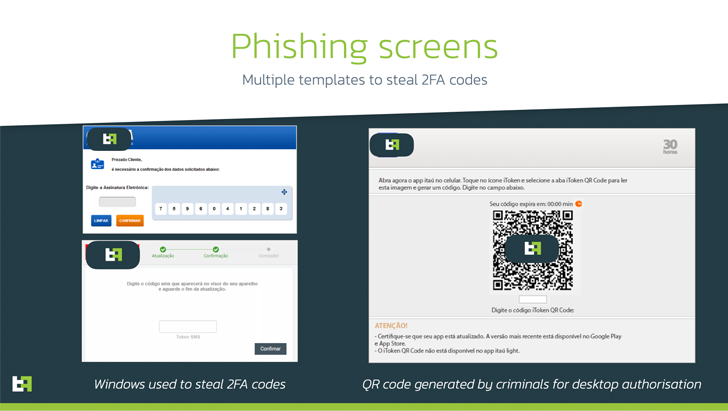
BrasDex’s ATS system was explicitly designed to abuse PIX technology to make fraudulent money transfers.
This is not the first time the instant payments ecosystem has been targeted by malicious actors. In September 2021, Check Point detailed two of his Android malware families named PixStealer and MalRhino. This family tricked users into transferring their entire account balance to an attacker-controlled account.
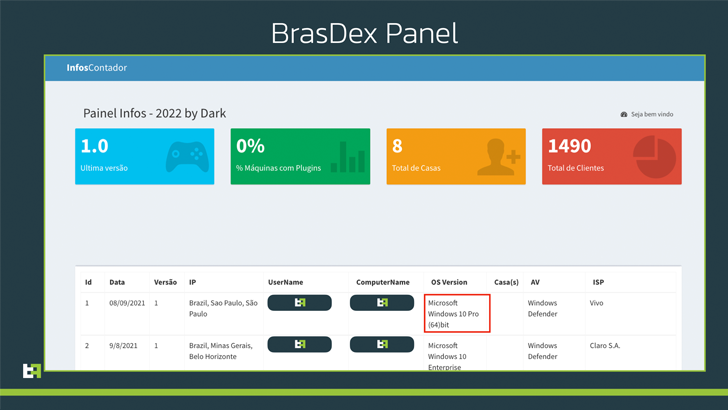
BrasDex research by ThreatFabric also provided access to C2 panels used by attackers to track infected devices and retrieve exfiltrated data logs from Android phones.
As it happens, the C2 panel has also been used to monitor another malware campaign that compromises Windows machines to deploy Casbaneiro, a Delphi-based financial Trojan.
This attack chain uses a phishing lure themed around the delivery of a parcel purporting to be from Correios, a state-owned postal service, following a multi-step process to trick recipients into running malware.
Casbaneiro’s capabilities include taking control of bank accounts, taking screenshots, performing keylogging, hijacking clipboard data, and acting as clipper malware to hijack crypto transactions. Allows you to run a range of typical backdoors.
“BrasDex and Casbaneiro, independent full-fledged malware families, form a highly dangerous pair, allowing the attackers behind them to target both Android and Windows users at scale,” ThreatFabric said.
“The BrasDex case illustrates the need to put fraud detection and prevention mechanisms on customer devices. It looks like something legitimate to the engine, because they’re done through the same devices that they normally use, and our customers are using it.”



