A Chinese nation-state group has been observed using HTML smuggling techniques to target European foreign ministries and embassies to deliver the PlugX remote access Trojan to compromised systems.
Cybersecurity firm Check Point describes the activity as “ Smag Xhas been ongoing since at least December 2022.
“This campaign uses new delivery methods (most notably HTML smuggling) to deploy a new variant of PlugX, an implant commonly associated with various Chinese threat actors,” said Check. Points Said.
“Although the payload itself is similar to that found in older PlugX variants, its delivery method has a low detection rate and has helped keep this campaign low profile until recently.”
The exact identities of the threat actors behind the operation are a bit vague, but existing clues point to the direction of the Mustang Panda, along with a cluster tracked as Earth Preta, Red Delta and Checkpoint’s own name Camaro Dragon. Duplicate.
However, the company said there was “insufficient evidence” at this stage to conclusively attribute it to hostile groups.
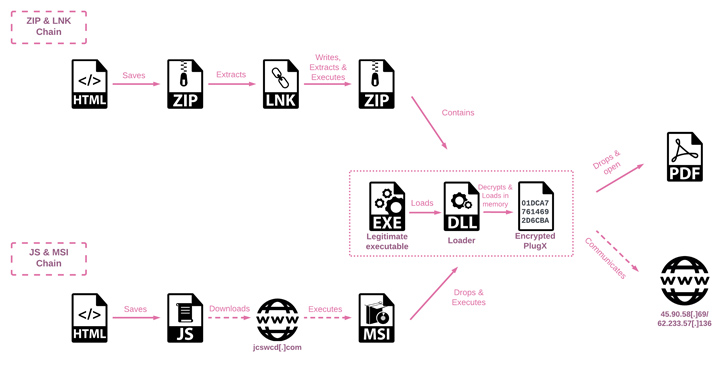
The latest attack sequence is HTML smuggling – Stealth techniques that exploit legitimate HTML5 and JavaScript functionality to assemble and launch malware within decoy documents attached to spear-phishing emails.
“HTML smuggling uses HTML5 attributes that work offline by storing binaries in immutable data blobs within JavaScript code,” said Trustwave. I got it early February of this year. “Data blobs, or embedded payloads, are decoded into file objects when opened in a web browser.”
Analysis of documents uploaded to the VirusTotal malware database reveals that it is designed to target diplomats and government agencies in the Czech Republic, Hungary, Slovakia, UK, Ukraine, and possibly France and Sweden. rice field.
In one instance, the threat actor allegedly used a Uyghur-themed lure (“China is trying to block the prominent Uyghur president at the United Nations. docx”). When the lure is opened, it beacons to an external server with an embedded invisible tracking function. Pixels for extracting reconnaissance data.
The multi-stage infection process utilizes a DLL sideloading method to decrypt and launch the final payload, PlugX.
Dating back to 2008, the malware, also known as Korplug, is a modular Trojan capable of “various plugins with different functionality” allowing operators to steal files, capture screens, log keystrokes, and Can execute commands.
“During the investigation of the sample, the attackers sent a batch script from the C&C server intended to wipe the traces of their activity,” Checkpoint said.
“This script, named del_RoboTask Update.bat, eradicates legitimate executables, PlugX loader DLLs, registry keys implemented for persistence, and eventually deletes itself. We believe this is a result of threat actors realizing they are under surveillance.” ”



