The infamous Emotet botnet has seen little activity for six months, delivering malicious spam. Let’s dig into the details and explain everything you need to know to fight the notorious malware.
Why is everyone scared of Emotet?
Emotet It is one of the most dangerous Trojan horses ever created. This malware has become a highly destructive program as it has grown in size and sophistication. Victims can be exposed to his campaign of spam emails, from corporate users to individual users.
Botnets distribute via phishing containing malicious Excel or Word documents. When users open these documents and enable macros, the Emotet DLL is downloaded and loaded into memory.
Find email addresses and steal them for spam campaigns. Additionally, botnets drop additional payloads such as Cobalt Strike and other attacks that lead to ransomware.
The polymorphic nature of Emotet and the many modules it contains make malware difficult to identify. The Emotet team is constantly changing tactics, techniques, and procedures to avoid existing detection rules. As part of its strategy to remain invisible to infected systems, malicious software uses multiple steps to download additional payloads.
And the consequences of Emotet’s actions are devastating to cybersecurity professionals. Removing malware is nearly impossible. It spreads rapidly, generates false indicators, and adapts according to the attacker’s needs.
How has Emotet been upgraded over the years?
Emotet is an ever-changing, highly modular botnet. This malware started its journey in 2014 as a simple banking Trojan.
- 2014. Money transfer, email spam, DDoS, address book theft modules.
- 2015. Evasion feature.
- 2016. Delivery of email spam, RIG 4.0 exploit kits, and other Trojan horses.
- 2017. Spreader and address book stealer modules.
- 2021. The malicious template for XLS used MSHTA and was dropped by Cobalt Strike.
- 2022. Some features have remained the same, but there have also been some updates this year.
This trend proves that Emotet isn’t going anywhere, despite frequent “holidays” and official shutdowns. Malware evolves rapidly and adapts to everything.
What features have been added in the new Emotet 2022 version?
After nearly half a year of hiatus, the Emotet botnet has gone from strength to strength. Here’s what you need to know about the new 2022 version.
- Drops IcedID, a modular banking Trojan.
- The malware loads XMRig, a miner that steals wallet data.
- Trojans have binary modifications.
- Emotet uses a 64-bit code base to bypass detection.
- Newer versions use new commands:
Calls rundll32.exe with a random named DLL and export PluginInit.
- Emotet’s goal is to retrieve credentials from Google Chrome and other browsers.
- It also aims to collect corporate data using the SMB protocol.
- Like six months ago, the botnet was using the XLS malicious lure, but this time it adopted a new lure.

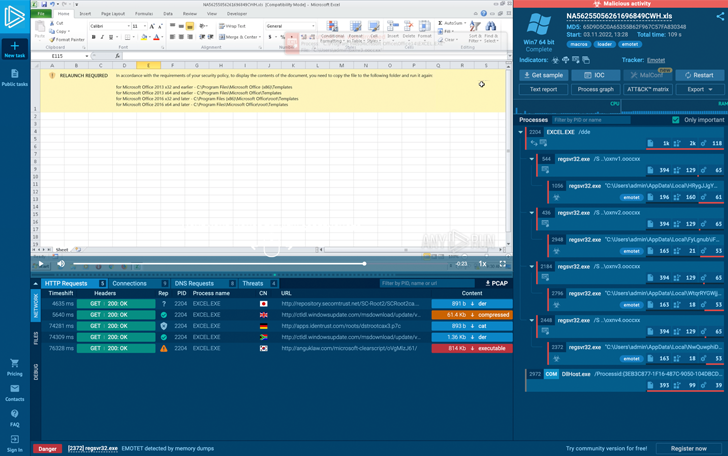 |
| Excel Lure for Emotet |
How to detect Emotet
Emotet’s main challenge is to detect it quickly and accurately in the system. In addition, malware analysts need to understand botnet behavior to prevent future attacks and avoid losses.
Emotet has strengthened its anti-evasion strategy with its long development story. Through the evolution of process execution chains and changes in malware activity within infected systems, malware has changed detection techniques significantly.
For example, in 2018 we were able to detect this bunker by looking at the name of the process. This was either:
eventswrap, implrandom, turnedavatar, sounder, archivesymbol, wabmetagen, msrasteps, secmsi, crsdcard, narrowpurchase, smxsel, watchvsgd, mfidlisvc, searchatsd, lpiograd, noticesman, appxmware, sansidaho
Then, in Q1 2020, Emotet began creating specific keys in the registry. Writes symbols (letter-letter) of length 8 to the value of the key HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER.
Of course, Suricata rules will always identify this malware, but detection systems often continue after the first wave as the rules need to be updated.
Another way to detect this banker was through malicious documents. Scammers used specific templates and lures and contained grammatical errors. One of the most reliable ways to detect Emotet is through YARA rules.
To overcome malware anti-evasion techniques and catch botnets, malware sandboxes are the most convenient tool for this purpose.of ANY RUNwhich not only detects, monitors and analyzes malicious objects, but also retrieves configurations already extracted from samples.
There are some features that I use exclusively for Emotet analysis.
- Revealing C2 links for malicious samples using FakeNet
- Correctly identify botnets using Suricata and YARA rulesets
- Get data about C2 servers, keys, and strings extracted from a sample memory dump
- Collect IOCs for new malware
This tool saves malware analysts valuable time by helping them perform investigations quickly and accurately.
ANY.RUN sandbox is Black Friday 2022Now is the perfect time to boost your malware analysis and save money! Checkout special offer Limited time offer from 22nd to 29th November 2022.

Emotet has not demonstrated full functionality and consistent subsequent payload delivery. Use modern tools like ANY.RUN online malware sandbox to improve your cybersecurity and effectively detect this botnet. Stay safe and do some proper threat hunting!


