North Korean state-sponsored hackers target think tanks, research centers, media outlets, and academics in the United States and South Korea for intelligence purposes.
A warning issued last week said the infamous Kimski hacker group (also known as Velvet Cholima, Thallium, and Black Banshee) is posing as journalists and stealing information through spear-phishing campaigns.
Warnings are displayed in the following format: joint recommendation Information from multiple agencies within the US and South Korean governments has revealed details of a recent hacking campaign by the Kimsuky group.
North Korean hackers create email addresses that closely resemble those of real individuals and send emails containing malicious documents and links disguised as reports and news articles.
However, the first approach often does not include links or attachments, instead aiming to gain the trust of the targeted victim.
This initial contact may include seeking answers to foreign policy-related inquiries, conducting research, requesting interviews, asking the recipient to review resumes and documents, or paying for writing a research paper. may appear as an attempt to offer
With such an approach, it is not uncommon to flatter the intended victim by mentioning being recommended as an expert source by another academic or researcher.
Disguised as journalists and broadcasters, the Kimski hackers sent messages about current affairs, such as whether North Korea was likely to return to talks with the United States and what to think about North Korea’s plans for a missile test. It can be framed as a question.
When the intended target responds to the email, they receive follow-up communications with dangerous links and booby-trapped Word documents attached.
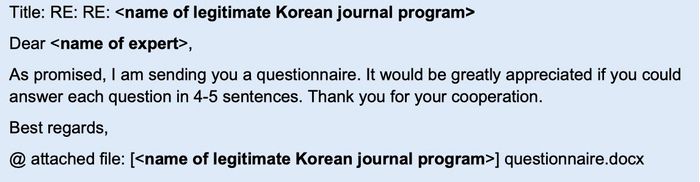
In another attack detailed in the advisory, North Korean hackers pretended to be South Korean academics, soliciting responses to investigations into North Korea’s nuclear program and demanding email interviews. It is said that there is
In such cases, follow-up emails may not only contain survey questionnaires, but also malicious payment forms.
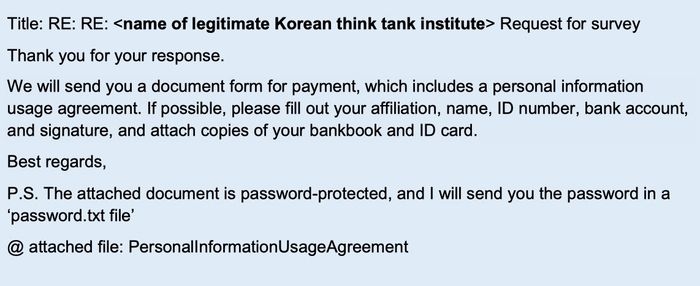
In this example, the malicious file is password protected to avoid detection by anti-malware software on email gateways.
The social engineering tactics hackers are using to respond to emails are: There are many more.
Additionally, users are advised not to enable macros on questionable documents and to be cautious about opening documents on cloud hosting services unless the message has been verified as legitimate.
The U.S. Department of Justice’s Judicial Awards Program offers the following awards: Up to USD 5 million Information about North Korea’s illegal activities in cyberspace.


