Malicious campaigns targeting the Middle East backdoor diplomacyis an APT (Advanced Persistent Threat) group with links to China.
The espionage campaign against telecommunications companies in the region is said to have started on August 19, 2021 with the successful exploitation of a ProxyShell vulnerability in Microsoft Exchange Server.
The initial compromise utilized binaries vulnerable to sideloading techniques, then used a combination of legitimate and bespoke tools to conduct reconnaissance, gather data, and laterally traverse the entire environment. to avoid detection.
Bitdefender researchers Victor Vrabie and Adrian Schipor report Share with Hacker News.
“Since February 2022, attackers have used different tools. [the] Quarian backdoors and many other scanners and proxy/tunneling tools. ”
BackdoorDiplomacy was first documented by ESET in June 2021. This incursion was primarily aimed at diplomatic agencies and telecommunications companies in Africa and the Middle East to deploy the Quarian (aka Turian or Whitebird).
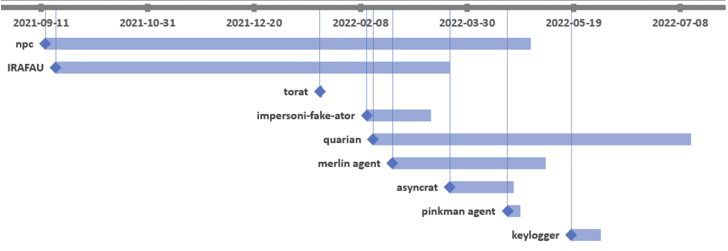
The attack’s espionage motivation is evidenced through the use of keyloggers and PowerShell scripts designed to collect email content. IRAFAU, the first malware component delivered after gaining a foothold, is used for information discovery and lateral movement.
This is facilitated by downloading and uploading files to and from command and control (C2) servers, launching remote shells and executing arbitrary files.
The second backdoor used in this campaign is an updated version of Quarian with a broader feature set for controlling compromised hosts.
A tool called Impersoni-fake-ator is also used and embedded in legitimate utilities such as: DebugView Putty, designed to retrieve system metadata and execute decrypted payloads received from C2 servers.
This intrusion is further characterized by the use of open source software such as: To Ratthe Golang remote management tool, and AsyncRATthe latter may be dropped via Quarian.
Bitdefender’s attribution of the attack to BackdoorDiplomacy comes from the duplication of C2 infrastructure that the group used in previous campaigns.



