For too long, the world of cybersecurity has focused exclusively on information technology (IT), leaving operational technology (OT) to do its thing. Historically, few industrial companies had a dedicated cybersecurity leader. All security decisions were left to the factory and factory management. While administrators are highly technical experts in other areas, they often lack cybersecurity training and knowledge.
In recent years, the rise in cyber-attacks on industrial facilities and the IT/OT convergence trend driven by Industry 4.0 have highlighted a ownership vacuum around OT security. According to a new report from Fortinetmost organizations look to their Chief Information Security Officer (CISO) to resolve issues.
Fortunately, CISOs are no strangers to change and daunting challenges. The position itself is less than 20 years old, but in those 20 years the CISO has navigated some of the most disruptive cybersecurity events that have been true tipping points in technology.
Yet most CISOs have a track record of securing IT environments, and IT security strategies and tools are rarely reflected in the context of OT. Soft skills in collaboration and team building certainly help CISOs as they incorporate the factory floor into their areas of responsibility, but they also make a focused effort to understand the unique topography and unique security challenges of OT environments. is needed.
Safety first
The three elements of CIA—confidentiality, integrity, and availability—are key concepts in cybersecurity. Importantly, although safety is always the common denominator, IT and OT prioritize the three factors differently.
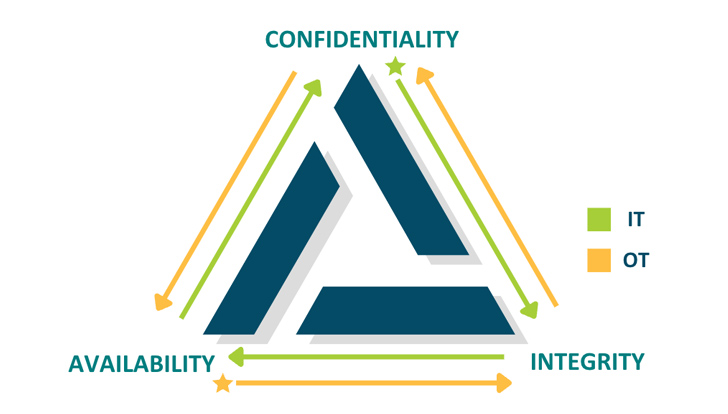 |
| Image 1: The CIA’s trilogy of IT security is flipped in the OT world where availability is paramount. |
- In IT, secure means data is protected by confidentiality. People get hurt when their sensitive personal data is compromised. For businesses, securing data protects them from breaches, fines, and reputational damage.
- Secure in OT means that cyber-physical systems are reliable and responsive. People get hurt when blast furnaces and industrial boilers don’t work properly. For businesses, availability keeps systems up and running on time in milliseconds, ensuring productivity and profitability.
Somewhat ironically, the AIC triad in the OT world has resulted in systems and tools that prioritize physical safety, but often have little or no cybersecurity capabilities. not provided. It is the responsibility of the CISO to identify and implement security solutions that protect OT systems from cyberthreats without disrupting operations.
Want to know how to protect your industrial operations from potential threats? Comprehensive report on I-SRA I have an answer. Uncover key challenges such as operational security risks and advanced persistent threats (APTs). download Today’s report!
level of segmentation
In both OT and IT, segmentation limits the attack surface of your network. In OT, purdue model It serves as a framework for how and why systems can communicate with each other.
In very simplistic terms, the Purdue model consists of five layers.
- Levels 4 and 5 are the outermost layers containing web and email servers, IT infrastructure, and remote user firewalls.
- Levels 2 and 3 are the operational layers that operate the software and applications that run the OT environment.
- Levels 0 and 1 include devices, sensors, programmable logic controllers (PLCs), and distributed control systems (DCS) that perform real work and need to be protected from external interference.
The purpose of these layers is to create logical and physical separation between process levels. The closer industrial systems such as injectors, robotic arms, and industrial printing presses are to cyber-physical operations, the greater the checks and balances to protect them.
The concept of segmentation is not new to CISOs, but they should understand that zone separation is stricter in OT environments and should always be enforced. Industrial companies adhere to the Purdue Model or other similar frameworks to ensure safety and security and to meet many regulatory compliance obligations.
Downtime is not an option
In IT, especially in the Software-as-a-Service (SaaS) world where new updates are released virtually in real-time, downtime for upgrades and patches is a non-issue.
Whether for safety or profit, OT systems are always on. They cannot be stopped or paused to download new operating systems or apply critical patches. A process that requires downtime is simply not a starter for most OT systems. For this reason, CISOs should be surprised to discover that a decades-old system (perhaps running software that reached its end-of-life date long ago) still functions as a critical part of the business. not.
The challenge facing CISOs is identifying security controls that do not disrupt or interfere with sensitive OT processes. A suitable solution is “Wrap” your existing OT infrastructure A layer of security that protects critical processes without changing, complicating or crowding them.
All access is “remote” access
Traditionally, OT systems have been protected by isolation. As organizations now connect these environments to take advantage of Industry 4.0 or to provide easy access for contractors, all access must be monitored, controlled and logged.
- The IT environment is the digital place where business takes place. Business users work in this space every day, and systems exchange data. In other words, a human is meant to actively participate in her IT environment and bring about changes in it.
- OT systems and environments are built to run without human intervention, allowing you to “set it and forget it.” Humans are designed to set them up and make them run. A user does not stay logged into her OT environment all day long, like a business user logs into her IT system.
In this context, the person accessing the OT environment effectively becomes an outsider. Any connection is external, be it a vendor connecting remotely, a business user accessing through the IT network, or her OT operator accessing the onsite environment. Recognizing this key point helps CISOs understand: Industrial Secure Remote Access (I-SRA) Tools should be used for all access scenarios, not just those that IT considers “remote.”
IT tools don’t (always) work for OT
Tools designed for IT are rarely applied to OT.
- Basic functions such as vulnerability scanning can disrupt OT processes and take systems completely offline. Also, most devices don’t have enough CPU/RAM to support endpoint security, antivirus, and other agents.
- Most IT tools route their traffic through the cloud. In OT, this can compromise availability and make it impossible to support the large number of disconnected components typical of OT environments.
- The life cycle of IT tools is typically much shorter than that of OT devices. Due to the always-on nature of OT environments, tools that require frequent patching, updates, or downtime cannot be applied.
Forcing IT-designed tools into OT environments only adds complexity without addressing the fundamental security requirements and priorities of these environments. The sooner CISOs realize that OT systems require security solutions designed for their unique needs, the sooner the right tools and policies will be deployed.
Soft skills are the key to CISO success
Given that most cybersecurity leaders today tend to assume IT security roles, it is not surprising that many CISOs hold a (perhaps unconscious) bias against IT philosophies, tools, and practices. Of course. To effectively secure the OT environment, CISOs must become students again and rely on others to learn what they don’t already know.
The good news is that CISOs typically push the envelope and want positive results, but they also tend to ask the right questions and seek support from the right experts. At the end of the day, the CISO’s job is to lead teams of people and professionals to achieve the larger goals of protecting the enterprise and enabling the business. Anyone willing to fill his OT security gap with strong leadership and a willingness to learn should be well on his way to success soon.
To learn about real-world solutions that can help CISOs secure their OT environments, visit discover the cholo.



