Five malicious Android dropper apps with over 130,000 cumulative installs have been spotted on the Google Play store distributing banking Trojans such as SharkBot and Vultur. They can steal financial data and carry out fraud on your device.
In a statement to The Hacker News, Dutch mobile security company ThreatFabric said, “These droppers continue the constant evolution of malicious apps that sneak up on official stores.
“This evolution includes overcoming restrictions by disguising itself as a file manager and sideloading malicious payloads via web browsers, according to newly introduced policies.”
These subjects dropper Includes 231 banking and cryptocurrency wallet apps from financial institutions in Italy, UK, Germany, Spain, Poland, Austria, US, Australia, France, and the Netherlands.
Dropper apps on official app stores such as Google Play are becoming an increasingly popular and efficient method of distributing banking malware to unsuspecting users. circumvent restrictions imposed by Google.

Below is a list of malicious apps, 4 of which are still available on digital marketplaces.
Since its start in October 2022, the latest wave of SharkBot attacks targeting banking users in Italy involved the use of a disguised dropper to identify the country’s tax laws (“Codice Fiscale 2022”).
Google’s Developer Program Policy states: REQUEST_INSTALL_PACKAGES permission To prevent it from being exploited to install arbitrary app packages, the dropper bypasses this barrier by opening a fake Google Play Store page spoofing the list of apps when it is launched, disguising itself as an update and launching the malware. Download
Outsourcing malware searches to browsers isn’t the only method criminals employ. In another example spotted by ThreatFabric, the dropper disguised itself as a file manager app. This is a category that is allowed to have the REQUEST_INSTALL_PACKAGES permission per Google’s revised policy.
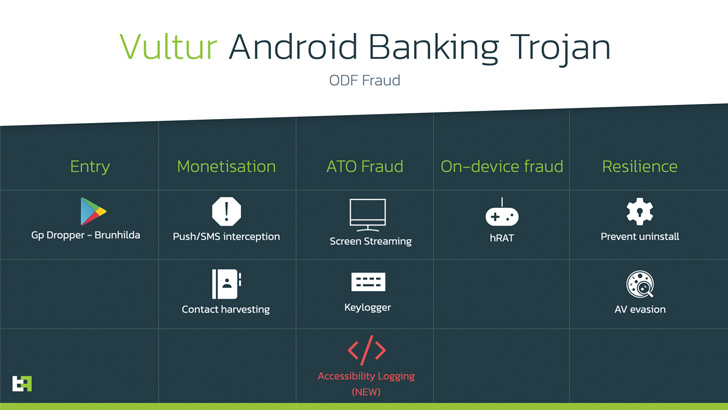
Three droppers have also been spotted that provide the advertised functionality, but with a secret feature that prompts users to install updates when they open the app and gives permission to install apps from unknown sources. also came with it, which led to the delivery of Vultur.
This new variant of the Trojan is notable for adding the ability to extensively record user interface elements and interaction events (clicks, gestures, etc.). FLAG_SECURE window flag Prevent banking apps from capturing screenshots.
Findings from ThreatFabric are also available as Cyble. It’s been found upgraded version of Drinik Android Trojan It targets 18 banks in India, masquerading as the official app of the country’s tax office and abusing accessibility service APIs to siphon personal information.
“Dropper distribution on Google Play continues to be the most ‘affordable’ and scalable way to reach victims for most of the different levels of actors,” the company said.
“Sophisticated tactics like telephone attack delivery are more resource-intensive and difficult to scale, but using droppers from official and third-party stores threat actors have a reasonable With hard work, you can reach a broader, unsuspecting audience.”



