Suspected Russian threat actors are targeting Eastern European users of the cryptocurrency industry to install information-stealing malware on compromised hosts, baiting bogus job opportunities.
According to Trend Micro researchers Aliakbar Zahravi and Peter Girnus, the attackers are “using a highly obfuscated custom loader in development to infect cryptocurrency industry players with the Enigma stealer.” said. Said in this week’s report.
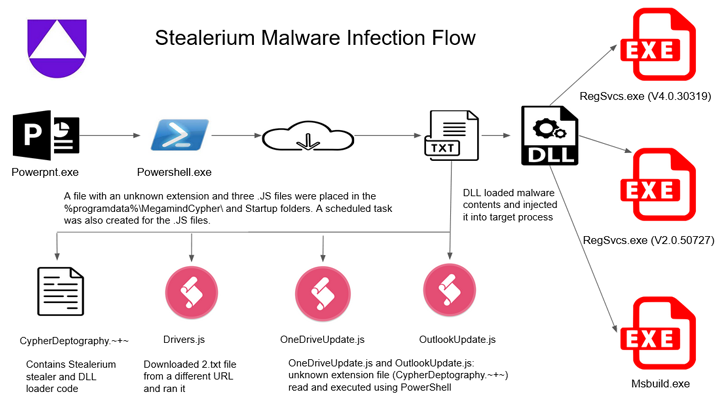
Enigma is said to be a modified version of Stealerium, an open-source C#-based malware that functions as a stealer, clipper, and keylogger.
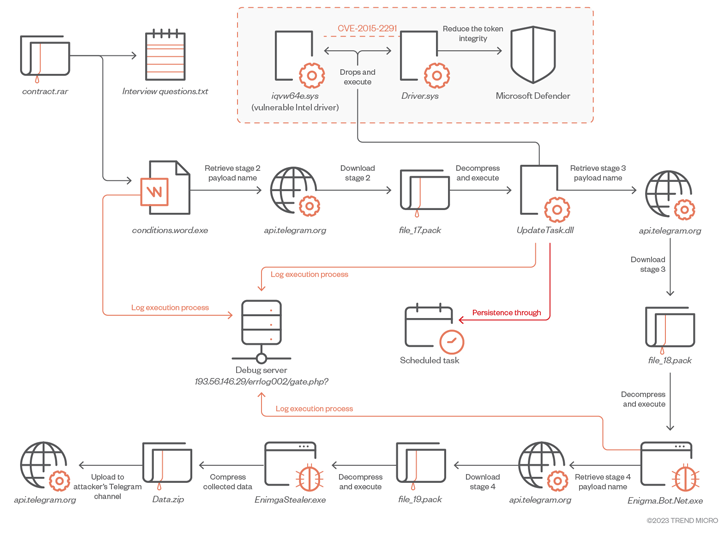
Complex infection vectors start with malicious RAR archive files distributed via phishing or social media platforms. It contains two documents, one of which is a .TXT file with a set of sample interview questions related to cryptocurrencies.
The second file is a Microsoft Word document that acts as a decoy and is responsible for launching the first stage Enigma loader. The first-stage Enigma loader then downloads and executes the obfuscated second-stage payload via Telegram.
“To download the next stage payload, the malware first sends a request to an attacker-controlled Telegram channel. […] “This approach allows attackers to continuously update and eliminate reliance on fixed filenames,” said the researchers.
A second-stage downloader that runs with elevated privileges disables Microsoft Defender by deploying a legally signed kernel-mode Intel driver that is vulnerable to CVE-2015-2291. Designed to be installed in 3 stages. technology called Bring Your Own Vulnerable Driver (BYOVD).
It is worth noting that the US Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to their Known Exploited Vulnerabilities (KEV) catalog, citing evidence of its exploitation in the wild.
The third stage payload finally paves the way for downloading the Enigma Stealer from an actor-controlled Telegram channel. This malware, like other stealers, has the ability to collect sensitive information, record keystrokes, and capture screenshots, all of which are stolen by Telegram.
Fake job offers are a tried and tested tactic employed by North Korea-backed Lazarus Group in attacks targeting the cryptocurrency sector. The adoption of this modus operandi by Russian threat actors “represents a persistent and lucrative attack vector.”
Findings are provided as Uptycs release Details of an attack campaign leveraging Stealerium malware to siphon personal data. This includes credentials for cryptocurrency wallets such as Armory, Atomic Wallet, Coinomi, Electrum, Exodus, Guarda, Jaxx Liberty, Zcash.
Joining Enigma Stealer and Stealerium to target cryptocurrency wallets is called another malware vector stealer It also has the ability to steal .RDP files, allowing attackers to perform RDP hijacking for remote access, Cyble said in a technical article.
Attack chains documented by cybersecurity firms show malware families being distributed via Microsoft Office attachments containing malicious macros, despite Microsoft’s efforts to close the loopholes. suggesting that malicious actors still rely on this method.
Similar methods are being used to deploy the Monero cryptominer against the backdrop of cryptojacking and phishing campaigns targeting users in Spain. Fortinet FortiGuard Lab.
The development is also the latest in a long list of attacks aimed at stealing victims’ cryptocurrency assets across platforms.
It consists of a “rapidly evolving” Android banking Trojan dubbed TgToxic that loots credentials and funds from cryptocurrency wallets as well as banking and financial apps. An ongoing malware campaign, active since July 2022, targets mobile his users in Taiwan, Thailand, and Indonesia.
“When a victim downloads a fake app from a website provided by the threat actor or attempts to send a direct message to the threat actor via a messaging app such as WhatsApp or Viber, cybercriminals can tricks you into registering, installing malware, and enabling the required permissions” Trend Micro Said.
Rogue apps are notable for not only abusing Android’s accessibility services to perform fraudulent money transfers, but also leveraging legitimate automation frameworks such as Easyclick and Auto.js to perform clicks and gestures. To do. This is the second Android malware after PixPirate to incorporate something like that. Workflow IDE.
However, social engineering campaigns can also be used as social media phishing and scams by setting up compelling landing pages mimicking popular crypto services with the goal of transferring Ethereum and NFTs from hacked wallets. Beyond Missing.
According to Recorded Future, this is accomplished by injecting cryptocurrency exfiltration scripts into phishing pages. The script lures victims into connecting their wallets with a lucrative offer to create non-fungible tokens (NFTs).
Such ready-made phishing pages are sold on darknet forums as part of so-called phishing-as-a-service (PhaaS) schemes, where other attackers rent out these packages to perform malicious operations at scale. It’s ready to run quickly.
“The ‘Crypto Drainer’ is a malicious script that acts like an e-skimmer and is deployed with phishing techniques to steal victims’ crypto assets,” the company said. Said A report released last week described the scam as being effective and growing in popularity.
“The use of legitimate services in a crypto drain phishing page can increase the likelihood that the phishing page will pass the “scam litmus test” of an otherwise savvy user. Once a crypto wallet is compromised, there are no safeguards to prevent unauthorized transfers of assets to an attacker’s wallet. ”
The attacks came as criminal groups stole a record-breaking $3.8 billion from cryptocurrency businesses in 2022, with much of the surge coming from North Korean government-backed hacking crews.


