Graham Cluley Security News reported this week, CorrideThank you to the amazing team for your support!
Here is an unpleasant fact. In most companies, employees can download sensitive company data to any device and keep it there forever, without even realizing they’re doing something wrong.
Kolide’s new report, “The State of Sensitive Data”sheds light on an often-ignored area of security, but nevertheless, there are gaping holes in many companies’ Zero Trust bastions.
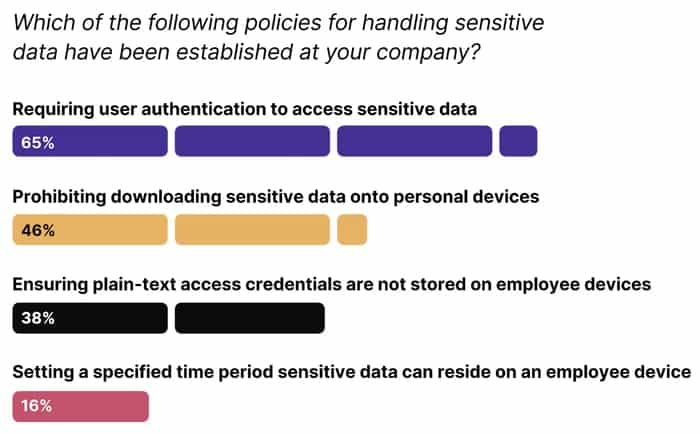
These findings are particularly alarming given the overall state of device security. IT teams struggle daily to enforce timely OS updates and patch management. This means end users store their most sensitive data, such as customer records, sensitive IPs, and plaintext access credentials, on devices that are vulnerable to attack.
This issue has not been addressed as there was no suitable solution until now. MDM solutions are way too blunt to handle sensitive data; and DLP tools are too extreme and invasive for most companies. After all, we are not trying to ban downloads all together, nor do we view all downloads as suspicious. Just make sure your employees don’t keep data on them longer than necessary or on unmanaged or insecure devices.
Kolide offers a more nuanced approach to setting and enforcing sensitive data policies.
Our premise is simple. If an employee’s device is not compliant, they will not be able to access the app.
Kolide allows admins to query and discover sensitive data, flag devices that violate policies, and force OS and browser updates to prevent vulnerable devices from accessing data can do.
Our unique approach makes device compliance part of the certification process. If the device is not compliant, the user will not be able to log in to cloud apps until the issue is resolved. But instead of adding more work for IT, Kolide provides instructions for users to unblock themselves.
To learn more and see the product in action, please visit: kolide.com.
If you’re interested in sponsoring my site for a week to reach IT-savvy users interested in computer security, you can find out more here.


