Advanced Persistent Threats (APT) group known as strong sympathy It targeted Android users with a Trojanized version of the Telegram app via a fake website masquerading as a video chat service called Telegram. shaggle.
“A copycat website mimicking the Shagle service is being used to distribute StrongPity’s mobile backdoor app,” said ESET malware researcher Lukáš Štefanko. Said in a technical report. “This app is a modified version of his open-source Telegram app, repackaged with StrongPity backdoor code.”
StrongPity, also known as APT-C-41 and Promethium, is a cyber espionage group that has been active since at least 2012, with the bulk of its activity focused on Syria and Turkey. The existence of this group was first officially reported by Kaspersky in October 2016.
of threat actors campaign The attack has since expanded to more targets in Africa, Asia, Europe, and North America, with the intrusion leveraging watering hole attacks and phishing messages to launch the kill chain.
One of StrongPity’s main features is to trick victims into downloading tainted versions of legitimate apps using fake websites that claim to offer various software tools.
December 2021, Minerva Laboratories disclosed A three-stage attack sequence that begins with the execution of a seemingly harmless Notepad++ setup file, ultimately delivering a backdoor to the infected host.
That same year, StrongPity Observed It deploys a piece of Android malware for the first time by infiltrating a Syrian e-government portal and replacing official Android APK files with their malicious counterparts.
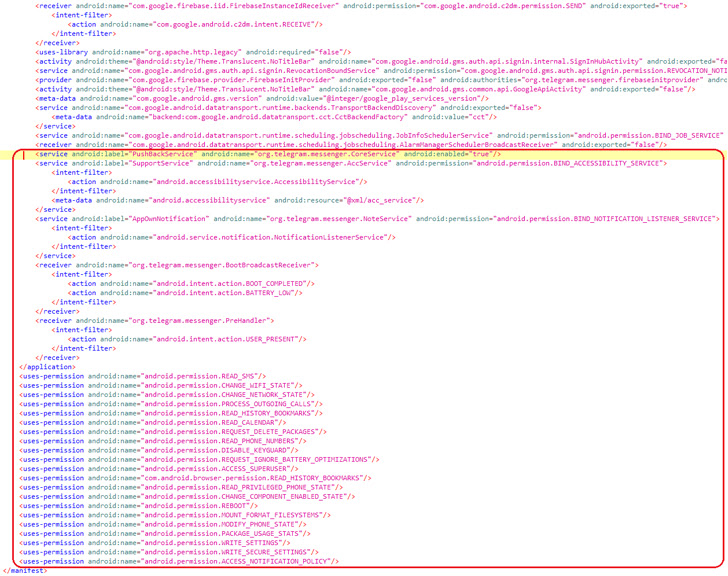
ESET’s latest findings were designed to distribute an updated version of an Android backdoor payload with call recording, device location tracking, SMS messages, call logs, contact lists, and file harvesting. It highlights a similar modus operandi.
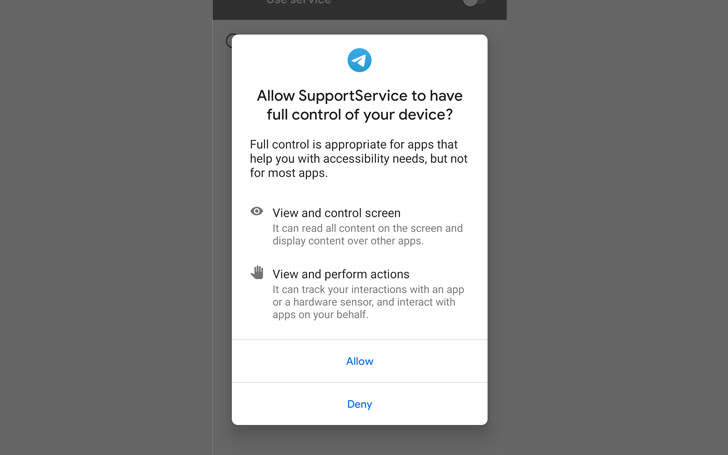
Additionally, granting accessibility service permissions to the malware allows it to siphon incoming notifications and messages from various apps such as Gmail, Instagram, Kik, LINE, Messenger, Skype, Snapchat, Telegram, Tinder, Twitter, Viber, and WeChat. can.
The Slovak cybersecurity firm describes the implant as modular, capable of downloading additional components from a remote command and control (C2) server to meet the evolving objectives of StrongPity’s campaign.
The backdoor functionality is hidden in the legitimate version of Telegram’s Android app, which became available for download on February 25, 2022. Lack of telemetry data.
There is also no evidence that the app was published on the official Google Play store. At present, it is not known how potential victims are directed to her fake website, or whether techniques such as social engineering, search engine poisoning, and fraudulent advertising are required. Hmm.
Also, the app (“video.apk”) has been published on the official Google Play store. It is currently unknown how potential victims were directed to her fake website, which included techniques such as social engineering, search engine poisoning, or deceptive advertising.
“Since the malicious domain was registered on the same day, it is possible that the copycat site and the fake Shagle app were available for download after that date,” Štefanko noted.
Another notable aspect of this attack is that the compromised version of Telegram uses the same package name as the real Telegram app. This means that backdoor variants cannot be installed on devices that already have Telegram installed.
“This could be done either by threat actors communicating with potential victims first and pushing them to uninstall Telegram from their devices if it is installed, or by campaigns focusing on countries where the use of Telegram for communication is rare. It can mean one of two things.


