A serious security flaw was discovered in the open source jsonwebtoken (JWT) library. Successful exploitation could lead to remote code execution on the target server.
“Using this VulnerabilityAn attacker could achieve remote code execution (RCE) on a server that validates a maliciously crafted JSON Web Token (JWT) request,” said Artur, a researcher at Palo Alto Networks Unit 42. Oleyarsh says. Said in Monday’s report.
tracked as CVE-2022-23529 (CVSS score: 7.6), this issue affects all versions of the library, including 8.5.1 and below, Version 9.0.0 Shipped December 21, 2022. This flaw was reported by a cybersecurity firm on July 13, 2022.
jsonwebtoken, i.e. Develop and maintain Okta’s Auth0.Done 10 million downloads every week It is registered in the npm software registry and used by over 22,000 projects.
Therefore, the ability to execute malicious code on a server violates confidentiality and integrity guarantees, allowing a malicious person to overwrite arbitrary files on the host and use a compromised private key to arbitrarily You may be able to take action.
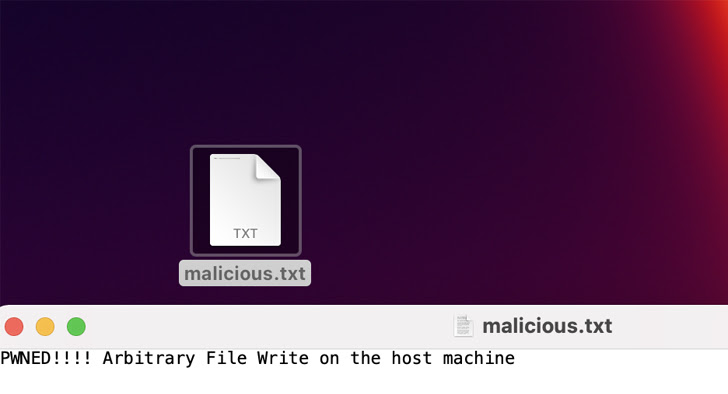
“Having said that, the vulnerability described in this post could be exploited to secretOrPublicKey valuethe attacker would have to exploit a flaw within the secret management process,” Oleyarsh explained.
As open source software increasingly emerges as a lucrative initial access vector for threat actors to mount supply chain attacks, vulnerabilities in such tools need to be proactively identified, mitigated, and patched by downstream users. It is important to apply
To make matters worse, cybercriminals have become much faster at exploiting newly revealed flaws, and the time between patch release and exploitation has been significantly reduced. According to Microsoft, it only takes an average of 14 days from the time a bug is made public until the exploit is actually detected.
To address this vulnerability discovery problem, Google last month launched OSV -Announced the release of Scanner.


