Russian cyber espionage group known as Turla It has been observed piggybacking on attack infrastructure used by decade-old malware to deliver its own reconnaissance and backdoor tools to Ukrainian targets.
Mandiant, owned by Google, tracks operations under the unclassified cluster moniker UNC4210said the hijacked servers corresponded to a variant of a commodity malware called ANDROMEDA (aka Gamarue) that was uploaded to VirusTotal in 2013.
“UNC4210 re-registered at least three expired ANDROMEDA command-and-control (C2) domains, began profiling victims, and selectively deployed KOPILUWAK and QUIETCANARY in September 2022,” said Mandiant. researcher Said In an analysis published last week.
Turla, also known as Iron Hunter, Krypton, Uroburos, Venomous Bear, and Waterbug, is an elite nation-state organization that primarily targets government, diplomatic, and military organizations using a number of custom malware.
Since the beginning of Russia’s military invasion of Ukraine in February 2022, this hostile group has been involved in a series of credential phishing and reconnaissance campaigns targeting organizations located within the country.
In July 2022, Google’s Threat Analysis Group (TAG) reported that Turla created a malicious Android app to allow pro-Ukrainian hacktivists to launch distributed denial of service (DDoS) attacks against Russian sites. announced that it supported
The latest findings by Mandiant show that Turla is stealthily employing old infections as a malware distribution mechanism. It goes without saying that it takes advantage of the fact that ANDROMEDA spreads via infected USB keys.
“USB-spreading malware continues to be a useful vector for gaining initial access to an organization,” said the threat intelligence firm.
In an incident analyzed by Mandiant, an infected USB stick was allegedly inserted into an unnamed Ukrainian organization in December 2021. Legacy ANDROMEDA Artifacts Launching a malicious link (.LNK) file masquerading as a folder in a USB drive can cause a
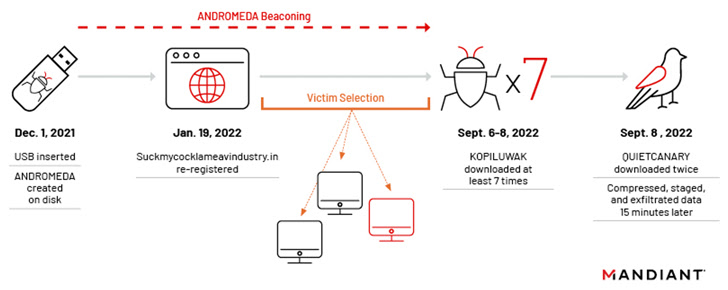
The threat actor then repurposed one of the dormant domains that were part of ANDROMEDA’s decommissioned C2 infrastructure and re-registered in January 2022. Kopiluwak Dropper, a JavaScript-based network reconnaissance utility.
Two days later, on September 8, 2022, the attack used a .NET-based implant called QUIETCANARY (aka Thunnus), exfiltrating files created after January 1, 2021.
The trading methodology employed by Turla is consistent with previous reports of the group’s extensive victim profiling efforts, which coincided with the Russian-Ukrainian war, and was used to gather information of interest to Russia. It may help coordinate subsequent exploitative activities.
It is also one of the rare instances in which a hacking unit has been identified that has targeted victims of another malware campaign to achieve its own strategic goals while masking its role.
“As older ANDROMEDA malware continues to spread from compromised USB devices, these re-registered domains are at risk as new threat actors may take control and deliver new malware to victims. ,” said the researchers.
“This new technique of claiming expired domains that are widely distributed and used by financially motivated malware may enable subsequent compromises at various entities. They are more likely to be overlooked by defenders triaging various alerts.”
COLDRIVER TARGETS US NUCLEAR LABORATORY
Findings are also available as Reuters report Another Russian government-backed threat group codenamed COLDRIVER (aka Callisto or SEABORGIUM) reportedly targeted three U.S. nuclear labs in early 2022.
As such, digital attacks created fake login pages for Brookhaven National Laboratory, Argonne National Laboratory, and Lawrence Livermore National Laboratory in an attempt to trick nuclear scientists into revealing their passwords.
This tactic is consistent with known COLDRIVER activity that recently uncovered spoofed login pages for defense and intelligence consulting firms, as well as NGOs, think tanks, and institutions of higher education in the UK and US.


