Threat actors associated with the Roaming Mantis attack campaign have been observed distributing updated variants of their patented mobile malware. Bulova Break into Wi-Fi routers and run the Domain Name System (DNS) hijack.
Kaspersky is analysis Malicious Artifact states that the feature is designed to target specific Wi-Fi routers located in South Korea.
Roaming Mantis, also known as Shaoye, is a long-running financial campaign that identifies Android smartphone users with malware capable of stealing bank account credentials and harvesting other types of sensitive information.
mainly Targeting the Asian region Since 2018, the hacking crew has been detected disguising the malware as a Google Chrome web browser application, expanding its reach to include France and Germany for the first time in early 2022.
This attack utilizes smishing messages as the initial intrusion vector to deliver malicious APKs or booby-trap URLs that redirect victims to phishing pages based on the operating system installed on the mobile device. Deliver.
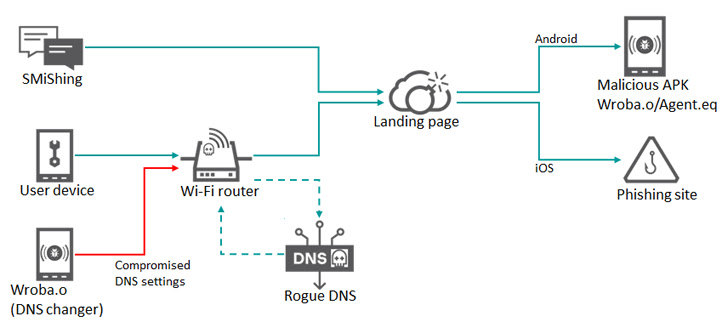
Some breaches also use Wi-Fi routers to lure unsuspecting users to fake landing pages. DNS hijackmanipulates DNS queries to redirect the target to the fake site.
Regardless of the method used, the intrusion paves the way for the deployment of a malware called Wroba (aka MoqHao and XLoader) with the ability to carry out numerous malicious activities.
According to the Russian cybersecurity firm, Wroba’s latest update includes a DNS changer feature designed to detect specific routers based on their model number and pollute their DNS settings.
“The new DNS Changer feature can manage all device communication with a compromised Wi-Fi router, including redirecting to malicious hosts and disabling updates for security products,” said a Kaspersky researcher. Suguru Ishimaru said.
The underlying idea is to redirect devices connected to a compromised Wi-Fi router to an attacker-controlled web page for further exploitation. Given that some of these pages deliver her Wroba malware, the attack chain effectively creates a steady stream of “bots” that can be weaponized to infiltrate healthy Wi-Fi routers. increase.
It’s worth noting that the DNS Changer program is only used in South Korea. However, the Wroba malware itself has been seen targeting victims in Austria, France, Germany, India, Japan, Malaysia, Taiwan, Turkey, and the United States via smishing.
Wroba is not the only mobile malware in the wild with DNS hijacking capabilities. In 2016, Kaspersky unmasked another of his Android Trojans. switcher It attacks the wireless routers of the network to which the infected device is connected and performs a brute force attack aimed at modifying the DNS configuration.
“Users with infected Android devices who connect to free or public Wi-Fi networks can spread malware to other devices on the network if the Wi-Fi networks they connect to are vulnerable. ‘ said the researchers.


