Details about a currently patched vulnerability in Azure Service Fabric Explorer have emerged (SFX), which can lead to unauthenticated remote code execution.
tracked as CVE-2023-23383 (CVSS score: 8.2), this issue has been named “Super FabriXss” by Orca Security based on the FabriXss flaw (CVE-2022-35829, CVSS score: 6.2) fixed by Microsoft in October 2022. I was.
“The Super FabriXss vulnerability allows remote attackers to exploit XSS vulnerabilities to remotely execute code in containers hosted on Service Fabric nodes without the need for authentication,” says a security researcher. author Lidor Ben Shitrit said. Said In a report shared with The Hacker News.
XSS is a kind of Client-side code injection An attack that allows malicious scripts to be uploaded to trusted websites. The script is then executed every time the victim visits the compromised website, leading to unintended consequences.
Both FabriXss and Super FabriXss are XSS flaws, but Super FabriXss has more serious implications in that it can be weaponized to execute code and take control of a susceptible system. .
Associated with each node in the cluster from the user interface[イベント]The Super FabriXss in the tab is also a reflected XSS flaw. That is, the script is embedded in the link and only triggered when the link is clicked.
“This attack is based on the Service Fabric platform.[Events]in the tab[Cluster Type Toggle]Option to allow an attacker to overwrite an existing Compose deployment by triggering an upgrade with a specially crafted URL from an XSS vulnerability,” explains Ben Shitrit.
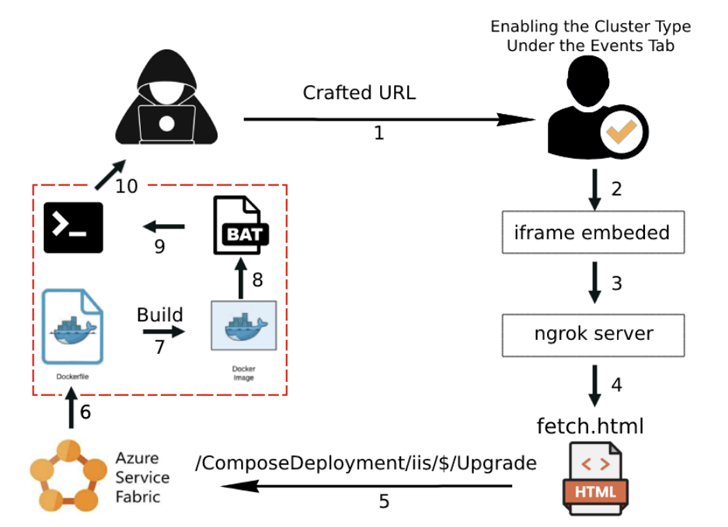
“By controlling a legitimate application in this way, attackers can use it as a platform to launch further attacks or gain access to sensitive data and resources.”
According to Orca, this vulnerability affects Azure Service Fabric Explorer versions 9.1.1436.9590 and earlier. It has since been addressed by Microsoft as part of the March 2023 Patch Monthly Update, with the tech giant describing it as a spoofing vulnerability.
“While the vulnerability is in the web client, malicious script executed in the victim’s browser translates into actions executed in the (remote) cluster.” I got it on that recommendation. “The victim user would have to click on her saved XSS payload inserted by the attacker.”
Become an Incident Response Pro!
Unlocking the Secrets of Bulletproof Incident Response – Master the 6-step process with Asaf Perlman, IR Lead at Cynet!
This disclosure states that NetSPI Privilege escalation flaw Allow users with “read-only” permissions to access sensitive information and execute commands in Azure Function Apps.
It also follows the discovery of an Azure Active Directory misconfiguration that exposed numerous applications to unauthorized access, including the content management system (CMS) that powers Bing.com.
Wiz, the cloud security company that codenamed the attack Bing Bangsays it can be weaponized to falsify Bing search results, or worse, even perform XSS attacks against users.


