The Transparent Tribe threat actor has been linked to a new campaign targeting Indian government organizations using a Trojan horse version of a two-factor authentication solution. Kabach.
Zscaler ThreatLabz researcher Sudeep Singh said, “This group is abusing Google ads for malvertising purposes and distributing a backdoor version of the Kavach multi-authentication (MFA) application.” increase. Said Analysis on Thursday.
According to a cybersecurity firm, advanced persistent threat groups have set up rogue websites spoofing the official Indian government website to trick unwitting users into entering their passwords, a small amount of credential harvesting. We are also attacking.
Also known as APT36, Operation C-Major, and Mythic Leopard, the Transparent Tribe is a suspected hostile group in Pakistan and has a history of attacking organizations in India and Afghanistan.
The latest attack chain isn’t the first time attackers have taken aim at Kavach (which means “armor” in Hindi). Essential app Users with email addresses in the @gov.in and @nic.in domains are required to sign in to email services as a second layer of authentication.
Earlier this March, Cisco Talos discovered a hacking campaign that used Kavach’s fake Windows installer as a decoy to infect government employees with CrimsonRAT and other artifacts.
One of their common tactics is to mimic legitimate governments, military, and related organizations to launch kill chains. The latest campaigns conducted by attackers are no exception.
“The attackers have registered multiple new domains that host web pages spoofing Kavach’s official app download portal,” said Singh. “They abused his Google Ads paid search feature to push malicious domains to the top of Google search results for Indian users.”
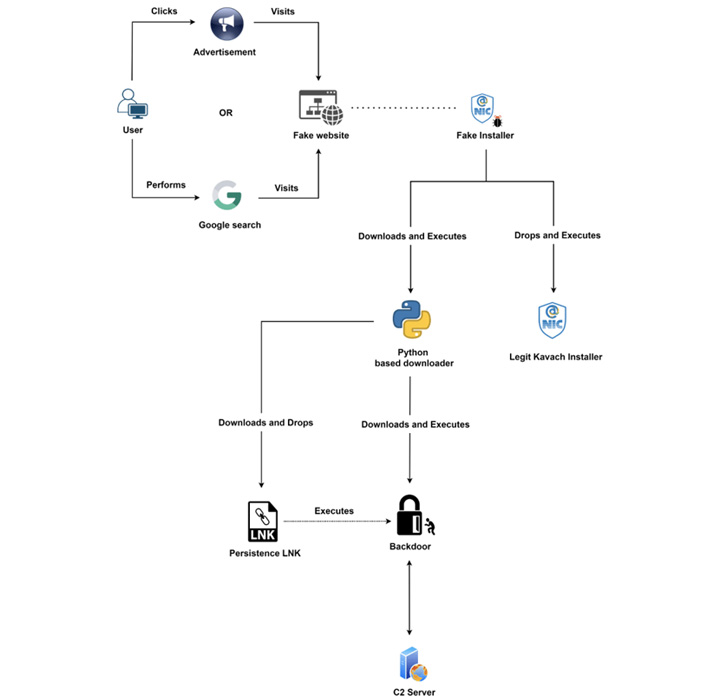
Since May 2022, Transparent Tribe has also allegedly distributed a backdoor version of the Kavach app through an attacker-controlled application store that claims to offer free software downloads.
The website also ranks high in Google searches, effectively acting as a gateway to redirect users looking for apps to rogue .NET-based installers.
Since August 2022, the group has used a previously undocumented data exfiltration tool, codenamed LimePad, designed to upload files of interest from infected hosts to the attacker’s servers. have also been observed.
Zscaler also says it has identified domains registered by Transparent Tribe. Kavach app login page This indicated that only accesses from Indian IP addresses were shown or that visitors were redirected to the home page of the National Informatics Center of India (NICs).
The page has the ability to capture victim-entered credentials and send them to a remote server to carry out further attacks against government infrastructure.
The use of Google Ads and LimePad demonstrates the attackers’ continuous attempts to evolve and refine their tactics and malware toolset.
“APT-36 continues to be one of the most prevalent advanced and persistent threat groups targeting users working for government agencies in India,” said Singh. “Applications used inside Indian government organizations are often the subject of social engineering used by the APT-36 group.”



