Since early 2020, a “massive and resilient infrastructure” consisting of over 250 domains has been used to distribute information-stealing malware such as Raccoon and Vidar.
The infection chain “uses around 100 fake cracked software catalog websites that redirect to several links before downloading the payload hosted on file-sharing platforms such as GitHub.” Says cybersecurity firm SEKOIA. Said In an analysis published earlier this month.
A French cybersecurity firm assessed the domain as being operated by a threat actor running a Traffic Direction System (TDS).
Targeting users searching for cracked versions of software and games on search engines such as Google, the attack uses a technique known as search engine optimization (SEO) poisoning to lure victims. Top up fraudulent websites by tricking them into downloading and executing malicious payloads.
The tainted results come with a download link to the promised software, which, when clicked, triggers a five-step URL redirect sequence that takes the user to a webpage displaying a shortened link. GitHub and its password.
“The use of multiple redirects complicates automated analysis by security solutions,” said the researchers. “This carving of the infrastructure is almost certainly designed to ensure resilience, making it easier and faster to update or change steps.”
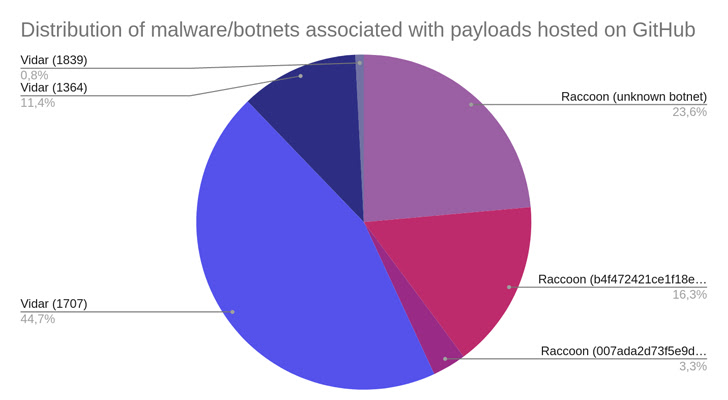
Once the victim unzips the RAR archive and runs the setup executable file it allegedly contains, one of two malware families, Raccoon or Vidar, will be installed on the system.
Development comes as Cyble Detailed A rogue Google Ads campaign that uses popular software such as AnyDesk, Bluestacks, Notepad++, and Zoom as lures to deliver a feature-rich stealer known as the Rhadamanthys Stealer.
Another variant of the attack chain has been observed utilizing phishing emails disguised as bank statements to trick unwitting users into clicking on malicious links.
Fake websites masquerading as popular remote desktop solutions have also been used in the past to spread malware known as Python-based information stealers. Mitsu Stealer.
Both malware are capable of siphoning various personal information from compromised machines, harvesting credentials from web browsers, and stealing data from various cryptocurrency wallets.
Users are advised to refrain from downloading pirated software and enforce multi-factor authentication wherever possible to harden their accounts.
“It is important that users exercise caution when receiving spam emails or visit phishing websites and verify the source before downloading any application,” said the researchers.


