Pakistan-based Advanced Persistent Threat (APT) actor known as . transparent tribe A two-factor authentication (2FA) tool used by an Indian government agency was used as a ruse to deliver a new Linux backdoor called Poseidon.
“Poseidon is a second stage payload malware associated with Transparent Tribe. report Published this week.
“This is a general-purpose backdoor that provides attackers with a wide range of capabilities to hijack infected hosts. Its capabilities include logging keystrokes, taking screen captures, uploading and downloading files, and various It includes remote management of the system in a variety of ways.”
Transparent Tribe, also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, has a track record of targeting Indian government agencies, military personnel, defense contractors, and educational institutions.
It has also repeatedly used a trojanized version of Kavach, a 2FA software mandated by the Indian government, to deploy various malware such as CrimsonRAT and LimePad to gather valuable information.
Another phishing campaign detected late last year utilized weaponized attachments to download malware designed to exfiltrate database files created by the Kavach app.
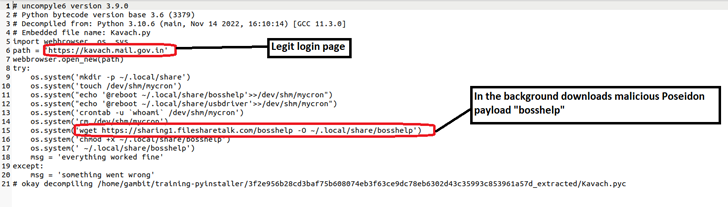
The latest series of attacks uses a backdoor version of Kavach to target Linux users working for government agencies in India. This indicates that the attackers are trying to expand their attack surface beyond the Windows and Android ecosystems.
“When a user interacts with the malicious version of Kavach, it redirects the user to a legitimate login page,” explains Sandapolla. “Meanwhile, the payload is downloaded in the background, compromising the user’s system.”
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – join us for this expert-led webinar!
The starting point of infection is ELF malware samplea compiled Python executable designed to get the second stage Poseidon Payload from a remote server.
The cybersecurity firm noted that the fake Kavach apps are mostly distributed through rogue websites masquerading as legitimate Indian government sites.This includes www.ksboard[.]and www.rodra[.]of.
As the primary attack vector used by the Transparent Tribe is social engineering, users working within the Government of India are advised to double-check any URLs received in an email before opening them.
“The impact of this APT36 attack is severe and can lead to sensitive information loss, system compromise, financial loss and reputational damage,” said Sandapolla.


