OpenAI revealed on Friday that a bug in its Redis open source library exposed other users’ personal information and chat titles on the startup’s ChatGPT service earlier this week.
of glitchIt was discovered on March 20, 2023.
“If both users were active around the same time, the first message of a newly created conversation could also appear in someone else’s chat history,” the company said. Said.
Additionally, this bug redis-py librarywhich leads to a scenario where the connection is broken due to the canceled request, and unexpected data (in this case, information belonging to an unrelated user) is returned from the database cache.
To make matters worse, a San Francisco-based AI research firm says it accidentally introduced a server-side change that caused a spike in request cancellations and increased error rates.
While the issue has since been resolved, OpenAI noted that the issue may have had more impact elsewhere, and announced that the issue would be resolved on March 20th from 1-10am PT. ) may have revealed payment-related information for 1.2% of ChatGPT Plus subscribers.
This included another active user’s first and last name, email address, payment address, last four digits of credit card number (only), and credit card expiration date. We emphasized that full credit card numbers are not published.
The company says it has reached out to affected users and notified them of the inadvertent leak. It also says, “Added redundant checks to ensure that the data returned from the Redis cache matches the requesting user.”
OpenAI fixes critical account takeover flaw
In another caching-related issue, the company has a severe account takeover vulnerability that can be exploited to take control of another user’s account, view chat history, and access billing information without their knowledge. We also dealt with gender.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
The defect is discovered By security researcher Gal Nagli, it bypasses protections introduced by OpenAI on chat.openai.[.]com to read the victim’s sensitive data.
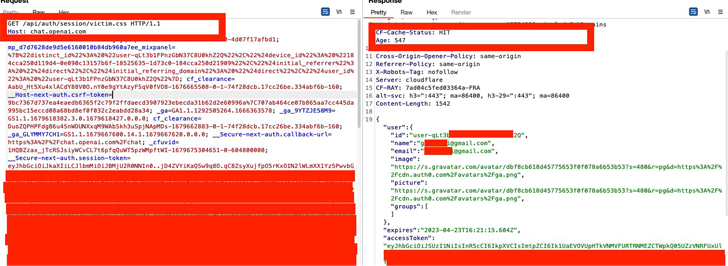
This replaces the .CSS resource with “chat.openai[.]com/api/auth/session/” endpoint, trick the victim into clicking a link, and cache the response containing a JSON object with the accessToken string. Cloudflare’s CDN.
Cached responses to CSS resources ( CF-Cache-Status header value set to HIT) is abused by attackers to obtain the target’s JSON Web Token (JWT) credentials and take over the account.
According to Nagli, the bug was fixed by OpenAI within two hours of responsible disclosure, indicating the seriousness of the problem.


