North Korea’s new state cyber operator has since 2018 resulted in a series of campaigns orchestrated to gather strategic intelligence consistent with Pyongyang’s geopolitical interests.
Mandiant, owned by Google, tracks activity clusters under monikers. APT43said the group’s motives were both espionage and financial motives, leveraging techniques such as credential harvesting and social engineering.
The financial aspect to attack campaigns is an attempt by threat actors to raise money to fulfill their “primary task of gathering strategic intelligence.”
The victim pattern suggests a concentration of targets in South Korea, the United States, Japan, and Europe, across government, education, research, policy organisations, business services, and manufacturing sectors.
This threat actor was also observed to veer off course by attacking health-related industries and pharmaceutical companies between October 2020 and October 2021, highlighting its ability to quickly change priorities. doing.
“APT43 is a prolific cyber operator that supports the interests of the North Korean regime,” said Mandiant researchers. Said In a detailed technical report released on Tuesday.
“Combining moderately sophisticated technical capabilities with aggressive social engineering tactics, the group consists of South Korean and US-based government agencies, academics, We are attacking think tanks.”
APT43’s activities are said to be consistent with North Korea’s foreign intelligence agency, the Reconnaissance General Bureau (RGB), and another hacking group and tactics called Kimsuky (aka Black Banshee, Thallium, or Velvet Chollima) It shows duplicates.
Additionally, it has been observed using tools previously associated with other subordinate adversarial syndicates within RGB, such as the Lazarus Group (aka TEMP.Hermit).
The attack chain launched by APT43 includes spear-phishing emails containing lures tailored to lure victims. These messages are sent using impersonations or fraudulent personas impersonating key figures within the target’s area of expertise in order to gain trust.
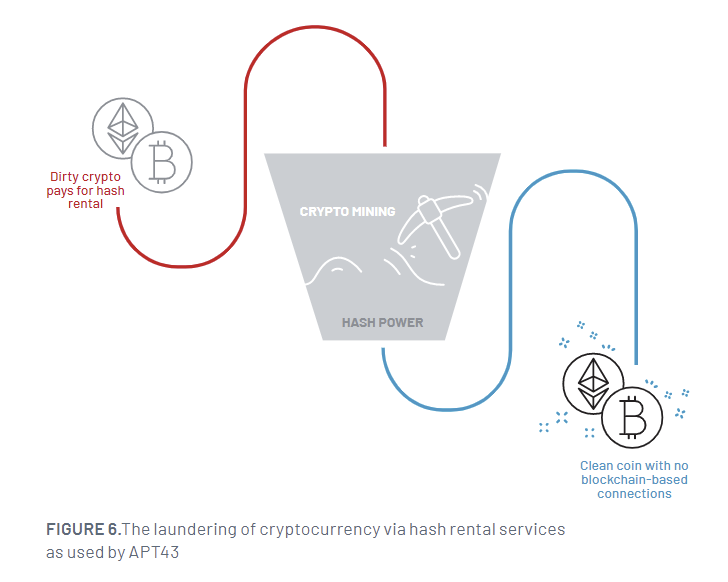
It has also been known to utilize contact lists stolen from compromised individuals to identify more targets and steal cryptocurrencies to fund attack infrastructure. is laundered in the following way: hash rental A cloud mining service that masks forensic trails and converts them into clean cryptocurrency.
The ultimate goal of the attack is to facilitate credential harvesting campaigns through domains that mimic various legitimate services and use the collected data to create online personas.
“The prevalence of financially motivated activity among North Korean groups has led to self-funding, even among groups that have historically focused on cyber espionage,” Mandiant said. It implies extensive obligations and the expectation of sustaining oneself without additional resources.
APT43’s operations are powered by a large amount of custom and public malware, including LATEOP (aka BabyShark), FastFire, gh0st RAT, Quasar RAT, Amadey, and an Android version of a Windows-based downloader called PENCILDOWN.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
The findings come less than a week after government agencies in Germany and South Korea warned of a cyberattack launched by Kimsuky using rogue browser extensions to steal users’ Gmail inboxes. I was.
“APT43 is highly responsive to the demands of the North Korean leader,” said the threat intelligence firm, noting that the group “maintains a high tempo of activity.”
“While spear-phishing and credential harvesting against government, military, and diplomatic organizations were the group’s primary missions, APT43 eventually adapted its targets and tactics, techniques, and procedures to suit its sponsors and Support the regime by carrying out financially motivated cyber crimes accordingly.”


