A new ransomware group known as RA Group is the latest actor to leverage the leaked Babuk ransomware source code to generate its own locker variant.
According to cybersecurity firm Cisco Talos, the cybercrime gang has been active since at least April 22, 2023, and is rapidly expanding its operations.
“To date, the group has compromised three US organizations and one South Korean organization across multiple industries, including manufacturing, asset management, insurance, and pharmaceuticals,” said security researcher Chetan Ragprasad. Stated. report I shared it with Hacker News.
RA Group is no different than other ransomware gangs in launching double extortion attacks and running date leaking sites to put additional pressure on victims to pay a ransom.
For Windows-based binaries, intermittent encryption Not to mention deleting the volume shadow copies and the contents of the machine’s Recycle Bin to speed up the process and avoid detection.
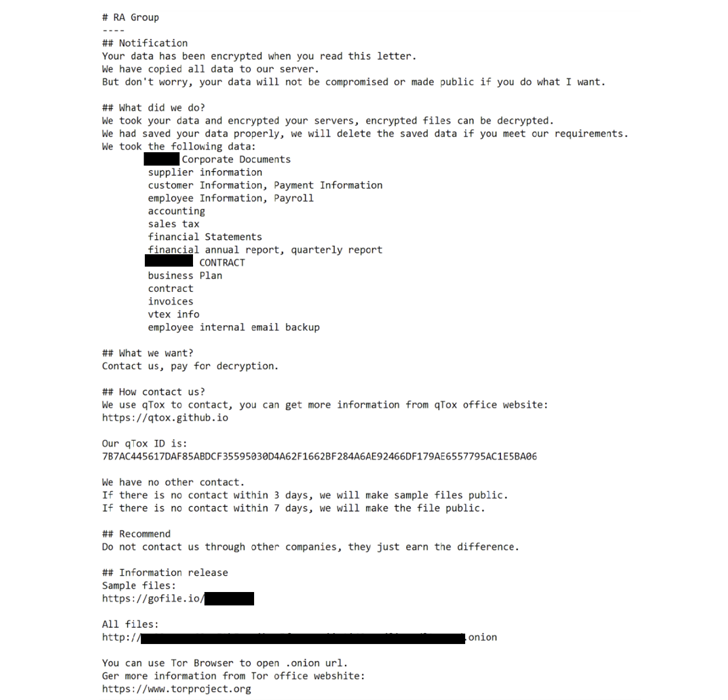
“RA Group uses a customized ransom note that includes the victim’s name and a unique link to download proof of exfiltration,” explained Rag Prasad. “If the victim does not contact the attacker within 3 days of her, the group will leak the victim’s files.”
It also takes steps to circumvent the encryption of system files and folders with a hard-coded list, allowing the victim to download the qTox chat application and use the qTox ID provided in the ransom note to access the operator. so that we can contact you.
What makes RA Group different from other ransomware campaigns is that the attackers have also been observed hosting information on secure TOR sites and selling exfiltrated victim data on leak portals. That’s it.
This development came less than a week after SentinelOne revealed attackers of varying sophistication and expertise. more and more hired Using the Babuk ransomware code, we have developed dozens of variants that can target Linux systems.
“Attackers are increasingly using the Babuk builder to develop ESXi and Linux ransomware,” said the cybersecurity firm. “This is especially noticeable when used by low-resource attackers, who are unlikely to significantly modify the Babak source code.”
Learn how to stop ransomware with real-time protection
Join our webinar to learn how to stop ransomware attacks using real-time MFA and service account protection.
Other ransomware actors that have adopted the Babuk source code over the past year include AstraLocker and Nokoyawa. His Cheerscrypt, another ransomware based on Babuk, is a short-lived ransomware for Rook, Night Sky, Pandora, and more. relevance has been pointed out.
The findings follow the discovery of two other new codenamed ransomware strains. Ranko’s and black suitThe latter is designed to target both Windows and VMware ESXi servers.
“The constant evolution and release of new ransomware variants highlights the high skill and agility of ransomware. [threat actors]This shows that we are responding to the cybersecurity measures and checks in place and customizing our ransomware accordingly,” Thybulle said.



