A new post-exploitation framework called EXFILTRATOR-22 (aka EX-22) has actually emerged with the goal of deploying ransomware inside corporate networks while flying under the radar.
“The breadth of functionality makes post-exploitation easy for anyone who purchases this tool,” CYFIRMA said. Said in a new report.
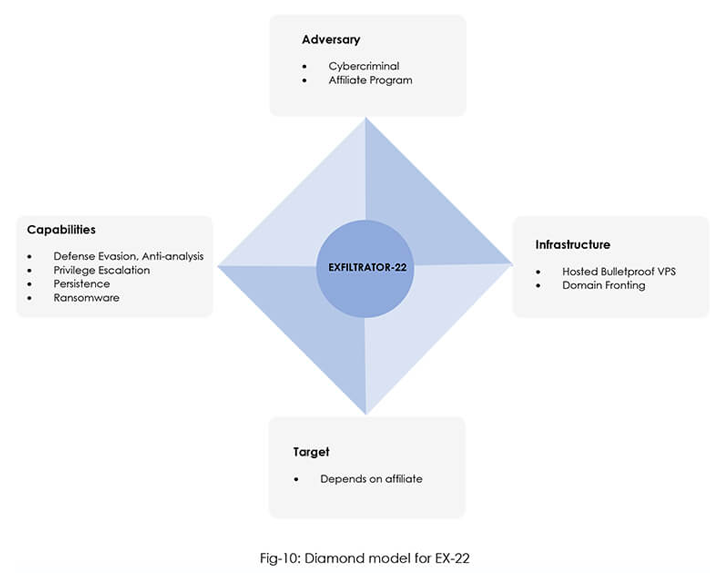
Notable features include establishing a reverse shell with elevated privileges, uploading and downloading files, logging keystrokes, launching ransomware to encrypt files, and live VNC (Virtual Network Compute Network) for real-time access. for example, starting a session.
It also has the ability to survive system reboots, perform lateral movement through the worm, view running processes, generate cryptographic hashes of files, and extract authentication tokens.
Cybersecurity firms have assessed with some confidence that the threat actors involved in creating the malware operate from the North, East, or Southeast Asia and are likely former affiliates of the LockBit ransomware company. bottom.
Advertised as completely undetectable malware on Telegram and YouTube, EX-22 is offered for $1,000 per month or $5,000 for lifetime access. Criminals who purchase the toolkit will be provided with a login panel to access the EX-22 server and remotely control the malware.
Since its first appearance on November 27, 2022, the malware author has continued to add new features to its toolkit, indicating active development work.
The connection to LockBit 3.0 stems from technical and infrastructure duplication, with both malware families leveraging the same. domain fronting A mechanism for hiding command-and-control (C2) traffic.
The Post-exploitation-framework-as-a-service (PEFaaS) model is the latest tool available to attackers looking to maintain covert access to compromised devices over time.
We also participate in other frameworks such as Manjusaka and Alchimist, as well as legitimate open source alternatives such as Cobalt Strike, Metasploit, Sliver, Empire, Brute Ratel, and Havoc that have been adopted for malicious purposes. increase.


