Update to encrypt more data for attackers after the US Cybersecurity and Infrastructure Security Agency (CISA) released a decryption tool to help affected victims recover from the ESXiArgs ransomware attack version recovered.
The emergence of new subspecies report Another participant came from an online forum system administrator who said that files larger than 128MB have 50% of the data encrypted, making the recovery process more difficult.
Another notable change is the removal of the Bitcoin address from the ransom note. The attackers are urging the victim to contact her on her Tox to get the wallet information.
The attackers “found researchers tracking their payments. They knew before releasing the ransomware that the encryption process of the original variant was relatively easy to circumvent.” There are possibilities,” Censys said. Said in writing.
“In other words, they are watching.”
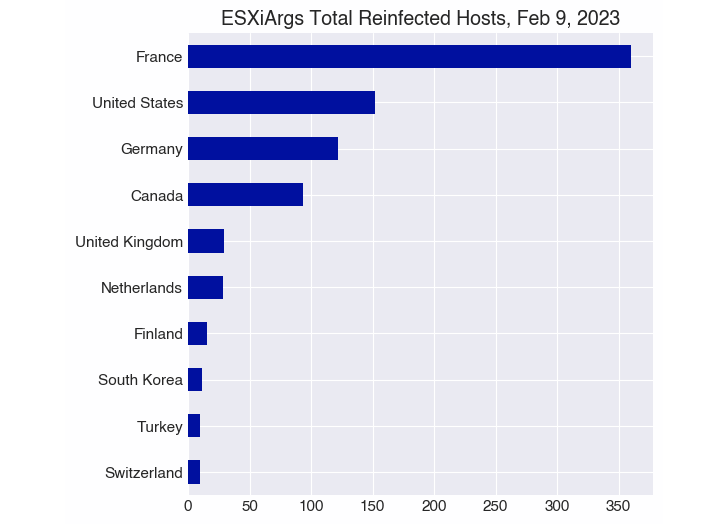
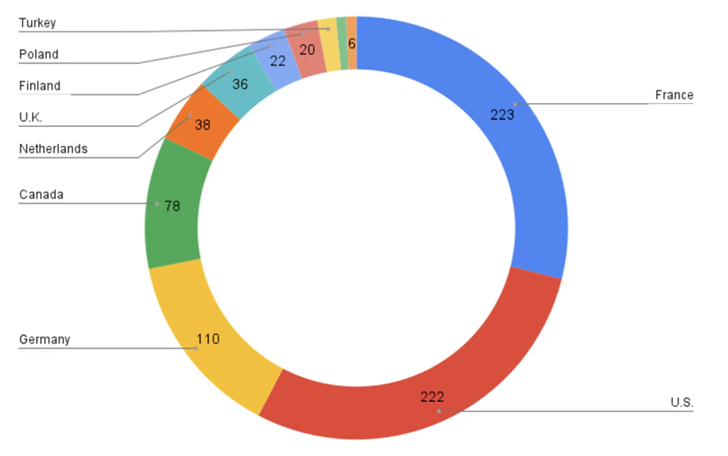
Statistics shared by crowdsourcing platform Ransomwhere evident As of February 9, 2023, 1,252 servers were infected with the new version of ESXiArgs, of which 1,168 were re-infected.
Over 3,800 unique hosts have been compromised since the ransomware outbreak in early February.a many Infections have occurred in France, the United States, Germany, Canada, the United Kingdom, the Netherlands, Finland, Turkey, Poland, and Taiwan.
ESXiArgs such as Cheerscrypt pride lockeris based on the Babuk Locker. Source code leaked of September 2021But the crucial difference from other ransomware families is the lack of data exfiltration sites. ransomware as a service (RaaS) model.
“The ransom is set at just over 2 Bitcoins (US$47,000) and the victim must pay within 3 days,” says cybersecurity firm Intel471 Said.
Initially, it was suspected that the intrusion involved exploiting an OpenSLP bug (CVE-2021-21974) that existed in VMware ESXi two years ago and is now patched, but the network discovery protocol Compromises have been reported on devices with disabled.
VMware later said it found no evidence to suggest that zero-day vulnerabilities in its software were being used to spread ransomware.
This indicates that the threat actors behind the activity may be exploiting some known vulnerabilities This makes it essential for users to quickly update to the latest version. These attacks have not yet been attributed to known attackers or groups.
“Based on the ransom note, the campaign is linked to a single threat actor or group,” says Arctic Wolf It pointed out“The more established ransomware groups typically run OSINT on potential victims before making an intrusion and set ransom payments based on perceived value.”
Cyber Security Company Rapid7 Said Discovered 18,581 internet-facing ESXi servers vulnerable to CVE-2021-21974 and further added that the RansomExx2 actor opportunistically targets vulnerable ESXi servers.
Tony Lauro, Director of Security Technology and Strategy at Akamai, said:
“The ESXiArgs ransomware is a prime example of why system administrators should patch as soon as they are released, and how long it takes for attackers to successfully launch their attacks.”


