A new malware called dotRunpeX Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, RemcosRhadamantis, Vidar.
“DotRunpeX is a new injector written in .NET using the Process Hollowing technique and used to infect systems with various known malware families”, Check Point Said In a report released last week.
Said to be in active development, dotRunpeX appears as a second stage malware in the infection chain, often a downloader (a.k.a. loader) sent via phishing emails as a malicious attachment. ) is expanded via
Or leverage malicious Google ads on search results pages to direct unsuspecting users searching for popular software such as AnyDesk or LastPass to mock sites hosting Trojanized installers. It is known that
The latest DotRunpeX artifact, first discovered in October 2022, uses the KoiVM virtualization protector to add an obfuscation layer.
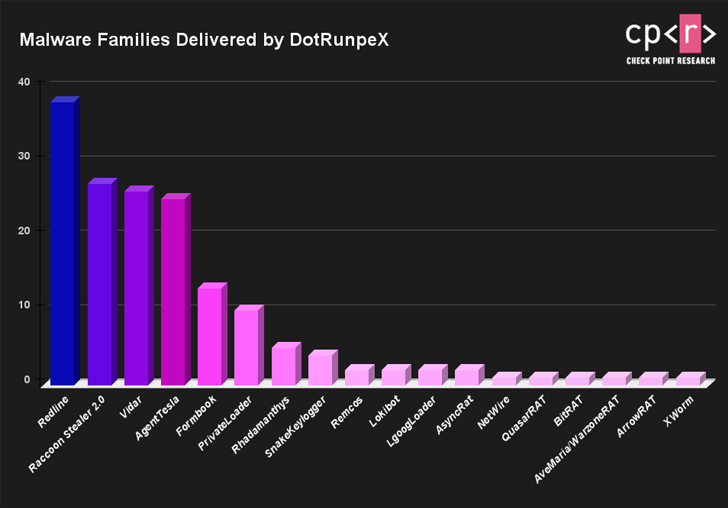
It’s worth pointing out that this finding is consistent with the malvertising campaign documented by SentinelOne last month.
Check Point’s analysis further revealed that “each dotRunpeX sample has an embedded payload of a specific malware family to be injected.” The injector specifies a list of antimalware processes to terminate.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize the risks.
this is, Vulnerable Process Explorer Driver (procexp.sys) built into dotRunpeX to get kernel mode execution.
Based on language references in the code, there are indications that dotRunpeX may be related to Russian-speaking actors. Malware families most frequently delivered by this new threat include RedLine, Raccoon, Vidar, Agent Tesla, and FormBook.


