So-called previously undetected APT (Advanced Persistent Threat) attackers red stinger Believed to be related to attacks targeting Eastern Europe since 2020.
“Military, transportation and critical infrastructure were some of the companies targeted and others involved in this incident. September Eastern Ukraine referendumpublished by Malwarebytes report Published today.
“In some campaigns, attackers were able to steal snapshots, USB drives, keyboard strokes, and microphone recordings.”
Red Stinger overlaps with the threat cluster that Kaspersky revealed last month under the name Bad Magic, which last year targeted government, agricultural and transport organizations in Donetsk, Lugansk and Crimea.
There have been indications that the APT group may have been active since at least September 2021, but Malwarebytes’ latest findings date back nearly a year to the group’s origins, with first activity dating back to December 2020. Done.
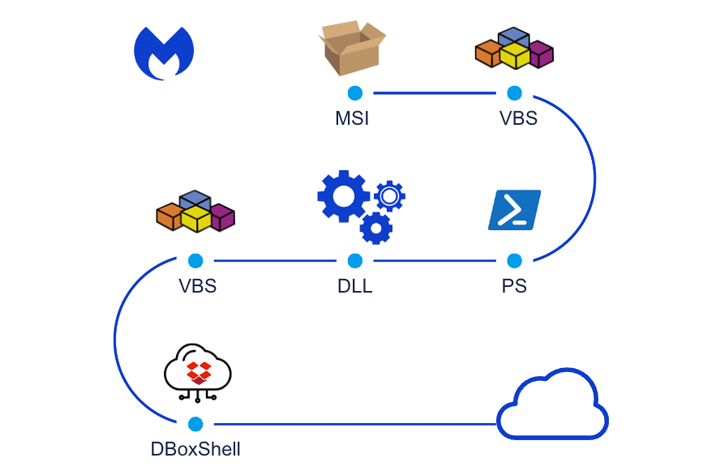
For years, the attack chain has leveraged malicious installer files to drop DBoxShell (aka PowerMagic) implants onto compromised systems. MSI files are downloaded using a Windows shortcut file contained within a ZIP archive.
Subsequent waves detected in April and September 2021 have been observed to utilize a similar attack sequence, albeit with minor differences in MSI filenames.
The fourth attack coincided with the launch of Russia’s military invasion of Ukraine in February 2022. The last known activity related to Red Stinger occurred in September 2022, as documented by Kaspersky.
“DBoxShell is malware that uses cloud storage services as a command and control (C&C) mechanism,” said security researchers Roberto Santos and Hossein Jaji.
“This stage acts as an entry point for attackers, allowing them to assess whether a target is interesting or not.
The fifth operation is also notable for providing an alternative to DBoxShell called GraphShell. GraphShell is so named because it uses the Microsoft Graph API for C&C purposes.
After the initial infection phase, threat actors deploy additional artifacts such as: Ngurok, rsockstun (a reverse tunneling utility), and a binary to exfiltrate the victim’s data to an attacker-controlled Dropbox account.
The exact scale of the infection is unknown, but evidence points to two victims in central Ukraine, a military target and a critical infrastructure worker, compromised as part of the February 2022 attacks. there is
Learn how to stop ransomware with real-time protection
Join our webinar to learn how to stop ransomware attacks using real-time MFA and service account protection.
In both cases, the attackers leaked screenshots, microphone recordings, and office documents after a period of reconnaissance. One of the victims had her keystrokes recorded and uploaded as well.
On the other hand, the fact that the September 2022 intrusion set primarily named regions allied with Russia, including officials and individuals involved in the election, is significant. In one of her monitored subjects, data was exfiltrated from a USB drive.
Malwarebytes said it also identified an infected library in the Ukrainian city of Vinnytsia as part of the same campaign, making it the only Ukrainian-affiliated entity targeted. The motive is currently unknown.
The origins of this threat group are shrouded in mystery, but sometime in December 2022, it became clear that the attacker infected his own Windows 10 machine either by accident or for testing purposes (named TstUser). rice field. their modus operandi.
Two things stand out. English is selected as the default language and the Fahrenheit temperature scale is used to display the weather. This probably suggests the involvement of native English speakers.
“In this case, it is not easy to attribute the attack to a specific country,” the researchers said. “Some victims are aligned with Russia and others with Ukraine, so either the country concerned or a linked group could be held responsible.”
“What is clear is that surveillance and data collection were the primary motives for the attack. It was clearly targeting a specific entity.”



