Various sectors of the East Asian market have been targeted in a new email phishing campaign distributing a previously undocumented Android malware variant. flu horse It exploits the Flutter software development framework.
“This malware features several malicious Android applications that mimic legitimate applications, most of which have been installed over 1,000,000 times,” said Check Point. Said in a technical report. “These malicious apps steal the victim’s credentials and her two-factor authentication (2FA) code.”
Malicious apps have been found mimicking apps such as ETC and VPBank Neo used in Taiwan and Vietnam. Evidence collected so far indicates that this activity has been active since at least May 2022.
The phishing scheme itself is fairly simple, with victims lured with emails containing links to fake websites hosting malicious APK files. The website also has additional checks aimed at screening the victim and delivering the app only if the browser has access to it. user agent string Matches that of Android.
Once installed, the malware requests SMS permissions and prompts the user to enter their credentials and credit card information. All this information is sent in the background to a remote server and the victim is asked to wait for a few minutes.
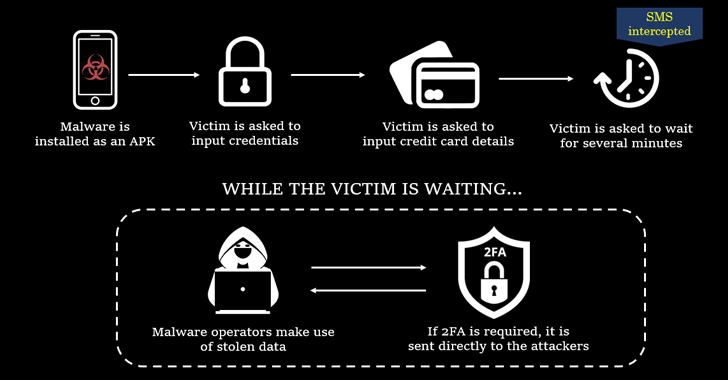
Attackers also exploited their access to SMS messages to intercept all incoming 2FA codes and redirect them to command and control servers.
An Israeli cybersecurity firm has also identified a dating app that redirects Chinese-speaking users to fraudulent landing pages designed to obtain credit card information.
Learn how to stop ransomware with real-time protection
Join our webinar to learn how real-time MFA and service account protection can stop ransomware attacks.
Interestingly, the malicious functionality is implemented as follows: flutteris an open source UI software development kit that can be used to develop cross-platform apps from a single codebase.
Threat actors are known to resist analysis and evade virtual environments using various tricks such as evasion techniques, obfuscation, and long delays before execution, but the use of Flutter brings a new level of sophistication. is shown.
“Malware developers put little effort into programming and relied on Flutter as a development platform,” the researchers concluded.
“This approach has allowed them to create malicious applications that are dangerous and largely undetected. One of the advantages of using Flutter is that its difficult-to-analyze nature makes many modern security solutions It becomes worthless.”



