Multiple vulnerabilities have been disclosed in Checkmk IT infrastructure monitoring software that could allow an unauthenticated, remote attacker to chain and take complete control of an affected server.
“These vulnerabilities could allow an unauthenticated, remote attacker to chain and execute code on a server running Checkmk version 2.1.0p10 or earlier,” said the SonarSource researcher. says Stefan Schiller. Said in technical analysis.
The open source version of Checkmk’s monitoring tool is based on Nagios Core, Nagbis Used to visualize and generate topology maps of infrastructure, servers, ports, and processes.
According to Munich-based developer tribe29 GmbH, its Enterprise and Raw editions are 2,000+ customersAirbus, Adobe, NASA, Siemens, Vodafone, etc.
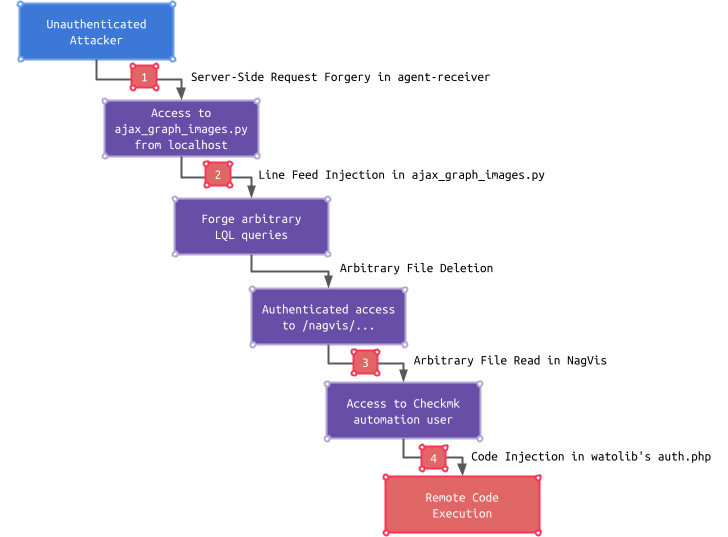
The four vulnerabilities, consisting of two severity bugs and two severity bugs, are:
These shortcomings themselves have limited impact, but adversaries can chain problems together. SSRF flaw Access an endpoint only reachable from localhost and use it to bypass authentication, read configuration files, and finally access the Checkmk GUI.
“This access could further turn into remote code execution by exploiting a code injection vulnerability in a Checkmk GUI subcomponent called watolib that generates a file named auth.php which is required for NagVis integration.” explains Schiller.
Four vulnerabilities were patched in Checkmk version 2.1.0p12 released on September 15, 2022, following a responsible disclosure on August 22, 2022.
The results of this survey are based on Zabbix and Isinga This could be exploited to execute arbitrary code and compromise the server.



